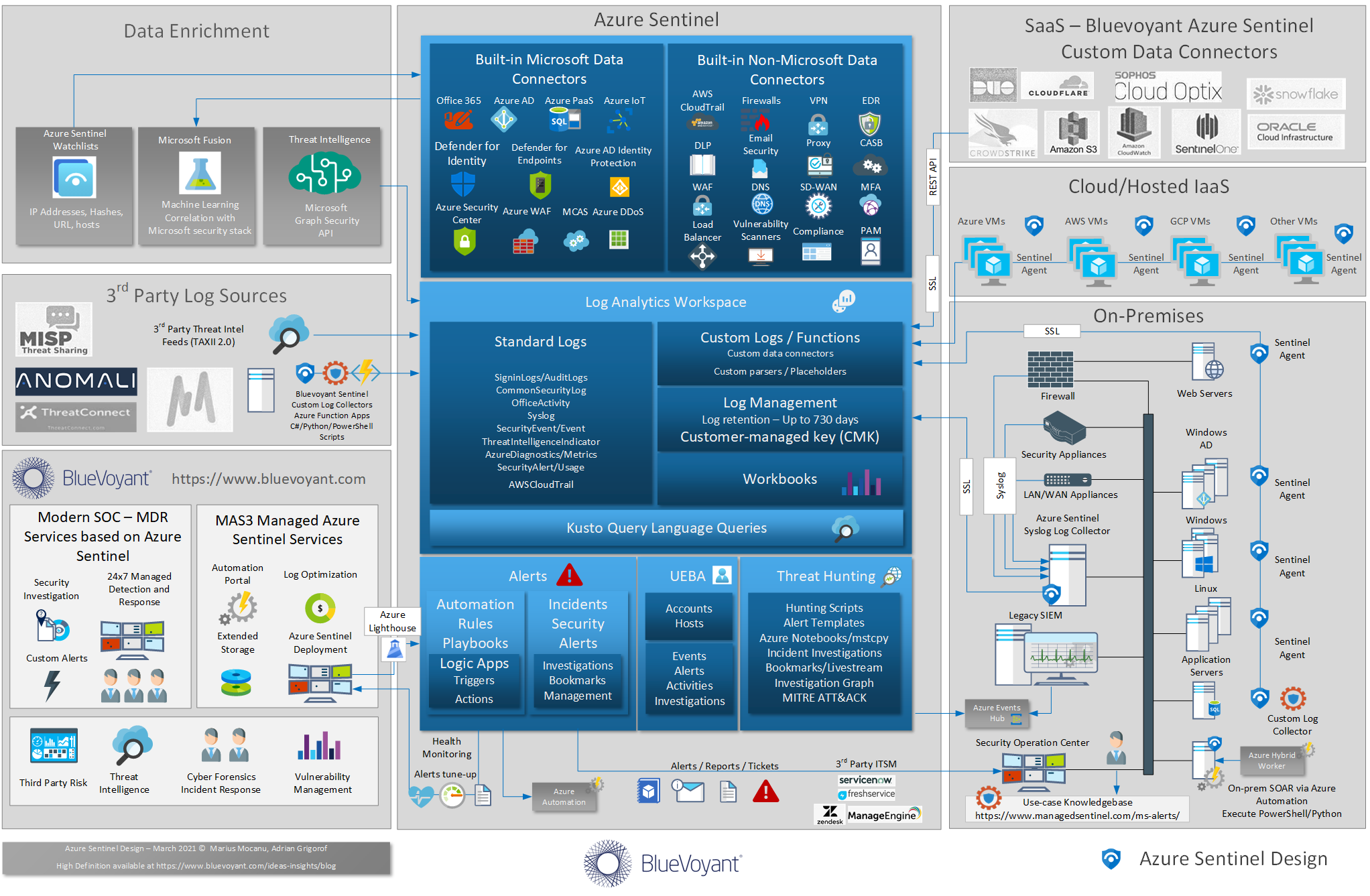
Azure Sentinel born-in-the-cloud SIEM was released in preview mode in February 2019 and in full general availability in September 2019, however, it has since advanced in bounds and leaps, doubling the number of data connectors, improving visualizations, incident management and building a rich ecosystem of options for SOAR and data enrichment. Combined with a tight […]
Author: Emily Young
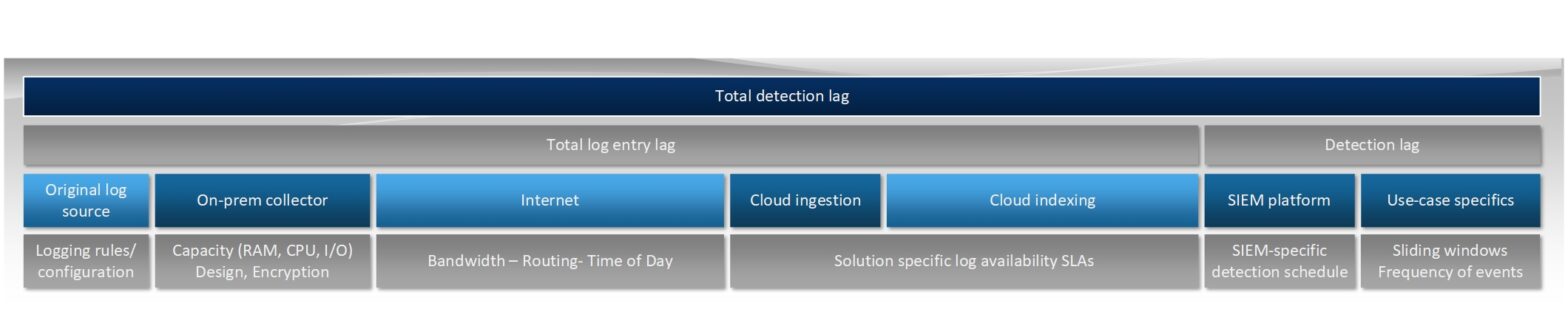
Log Ingestion Lag in Cloud-Based SIEMs
Lag in log ingestion is a topic that comes up now and then in our Azure Sentinel design discussions with our customers. We even had concerns around the speed of light being a constrain for certain critical log sources. These would be valid for security controls designed to protect strategic infrastructure but one has to […]
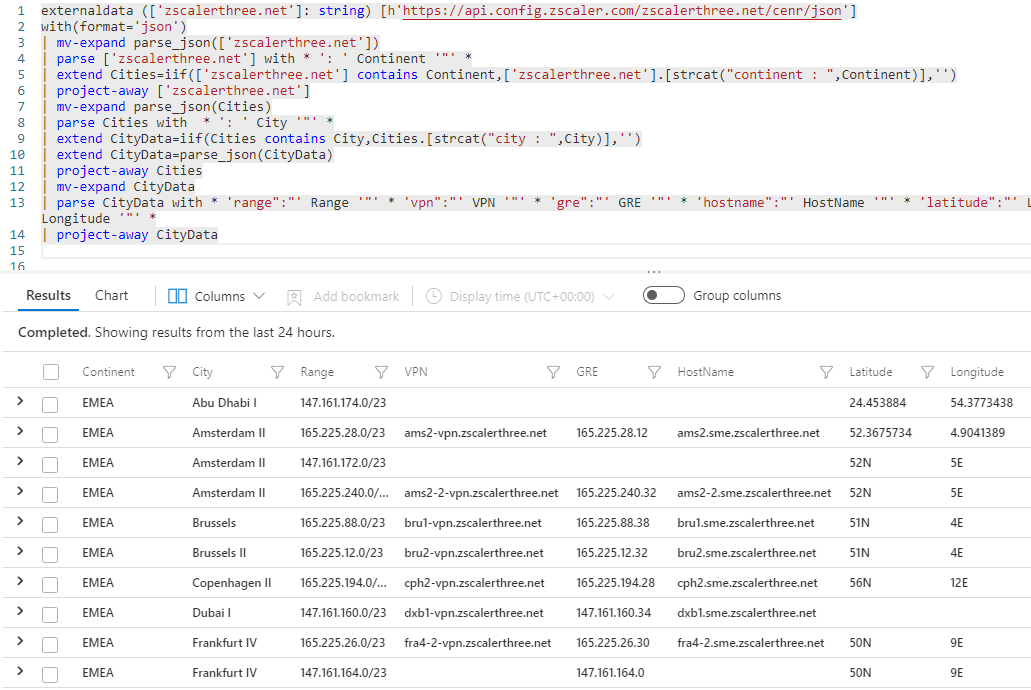
Using KQL to Ingest External Data In Azure Sentinel
One of the most sought-after features of a modern SIEM is the ability to read data from various Internet-based sources and use it to enrich the analysis of the raw logs. Such resources could come in various “packages” – they could be freely downloadable files or they may require authentication tokens/paid subscriptions, some are CSV, […]
Microsoft Security Stack Coverage
Contact us for full walk-through of this diagram and a review of Microsoft Graph Security integration with the overall Microsoft security stack.
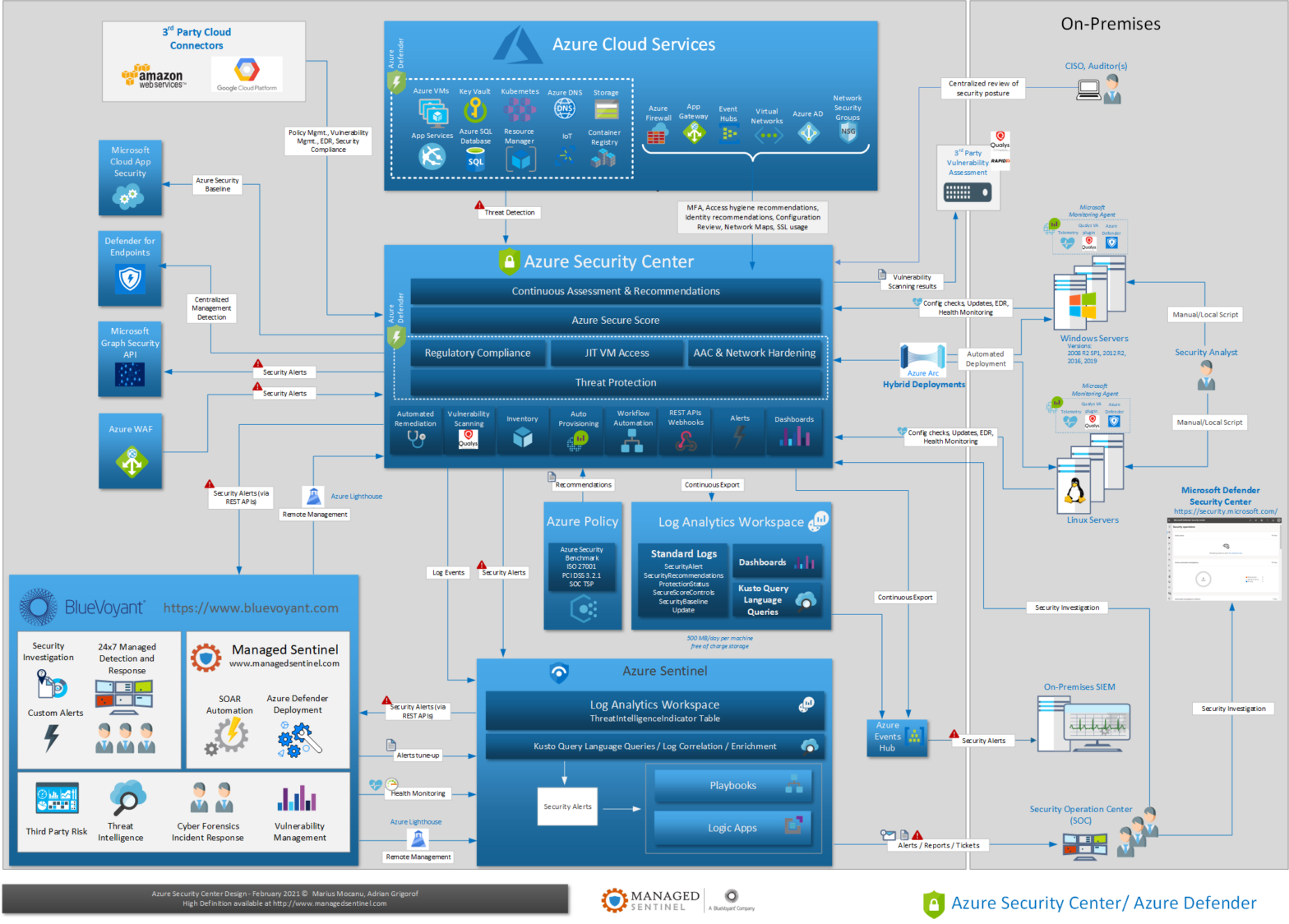
Azure Security Center Design
This post is a second iteration on Azure Security Center (ASC), part of our effort to provide one-page diagrams for Microsoft’s M365/Defender (aka XDR) components. In our first post on ASC, we mentioned how one of the most common questions that we are receiving about Azure Sentinel is about its functionality compared with Azure Security […]
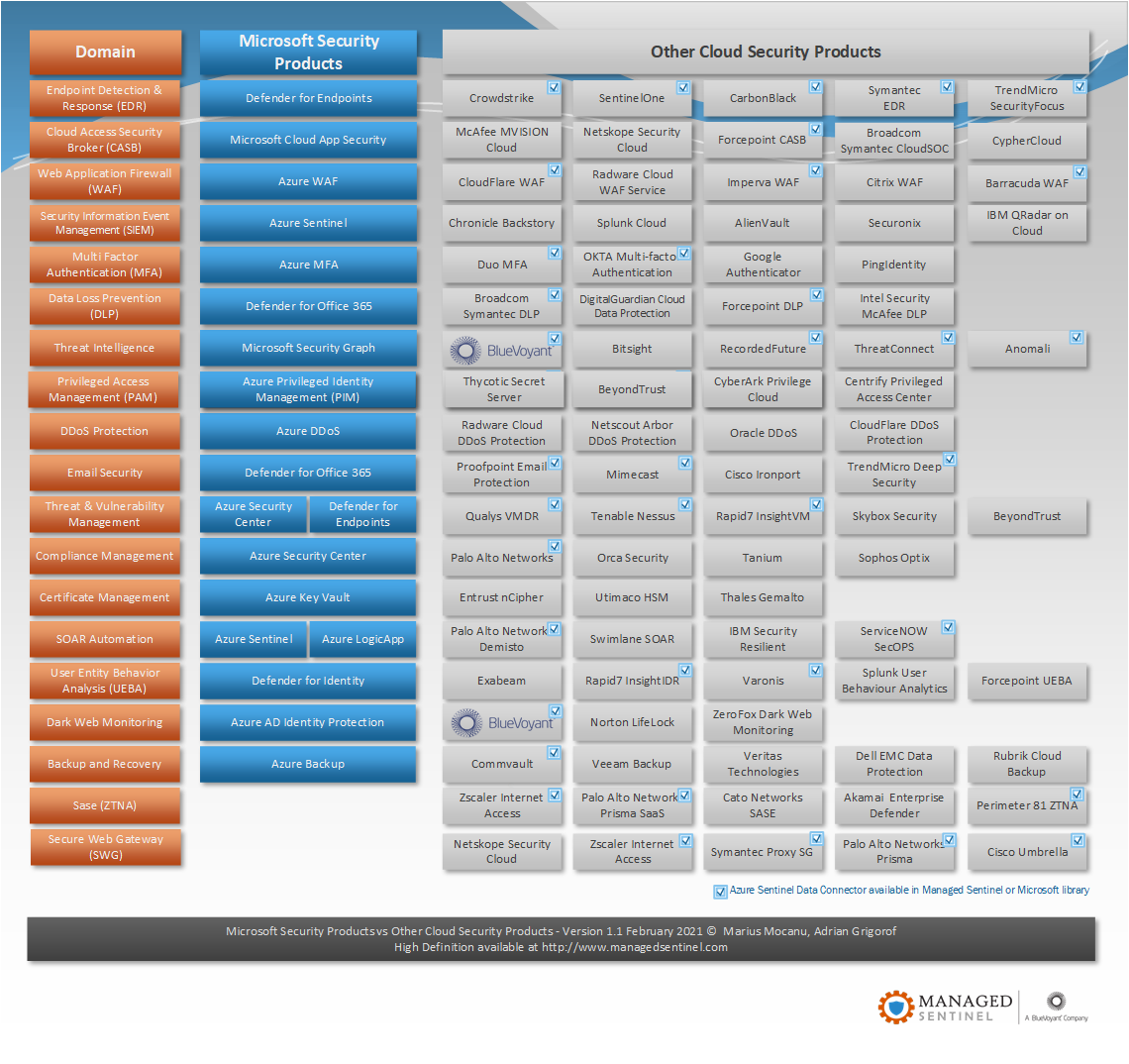
Microsoft Security Products vs. Other Cloud Security Products
In recent years, Microsoft has emerged as a market leader for a wide range of security areas, with a high focus on the hybrid infrastructure. In the diagram below, we are attempting to map each of the Microsoft security products to products to other vendors that have a significant market presence. Some of them are […]
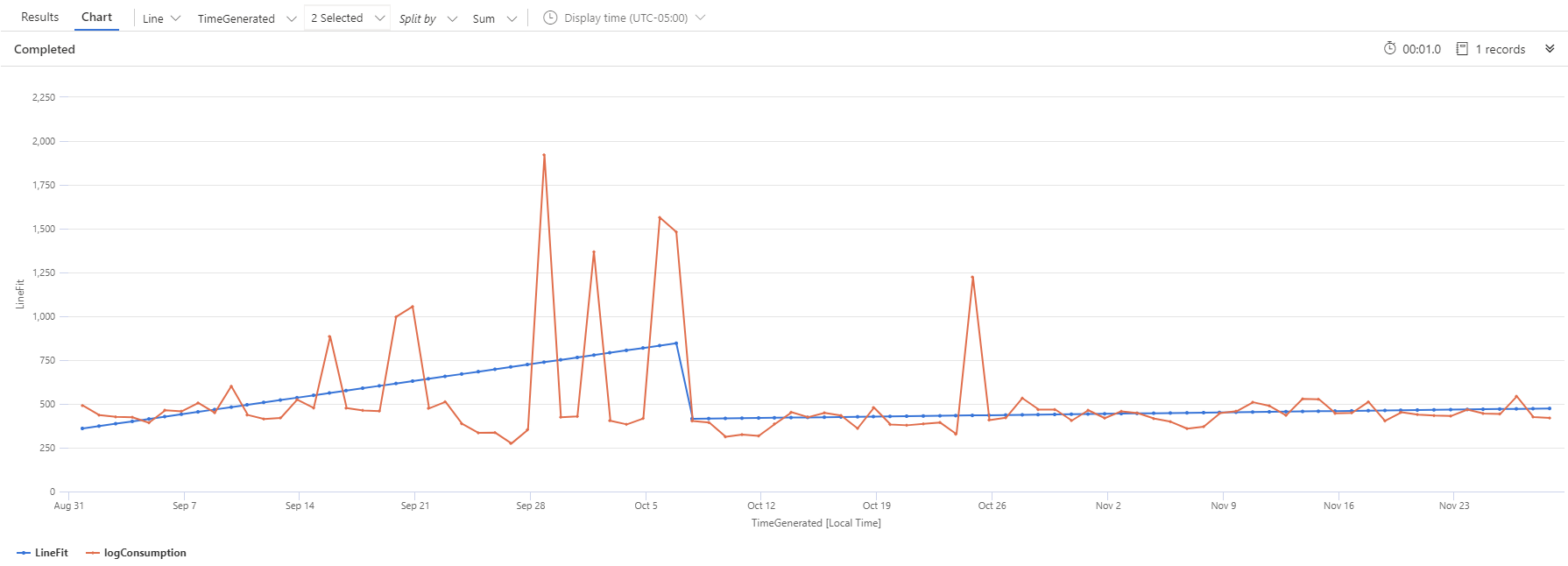
Using KQL to Estimate Log Ingestion Volume In Azure Sentinel
Azure Sentinel pricing model is driven by the amount of data ingested for security analytics that is stored in the related Log Analytics workspace. Given the costs of the cloud resources, it is important to be able to estimate future logs space consumption and consider any budget-related implications. Basing the analysis on the past data, […]
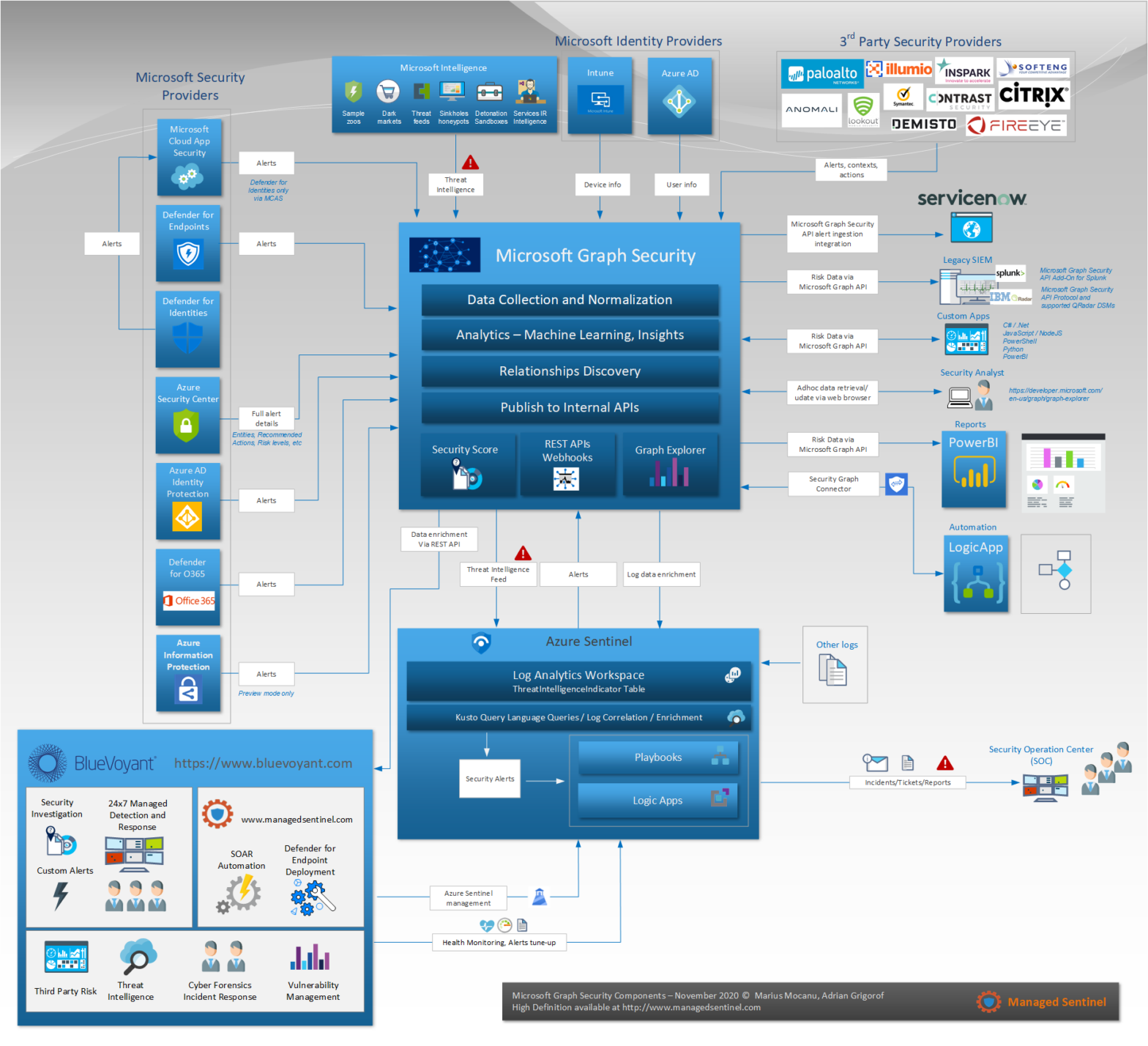
Microsoft Graph Security Components & API
Microsoft Graph, the Security component was born as a way to represent the threat intelligence information in a form that is closer to the way they attackers approach their targets, as a graph of interconnected systems, with complex relationships between themselves and 3rd party entities. Inside the graph, Microsoft is using their substantial analytical power […]
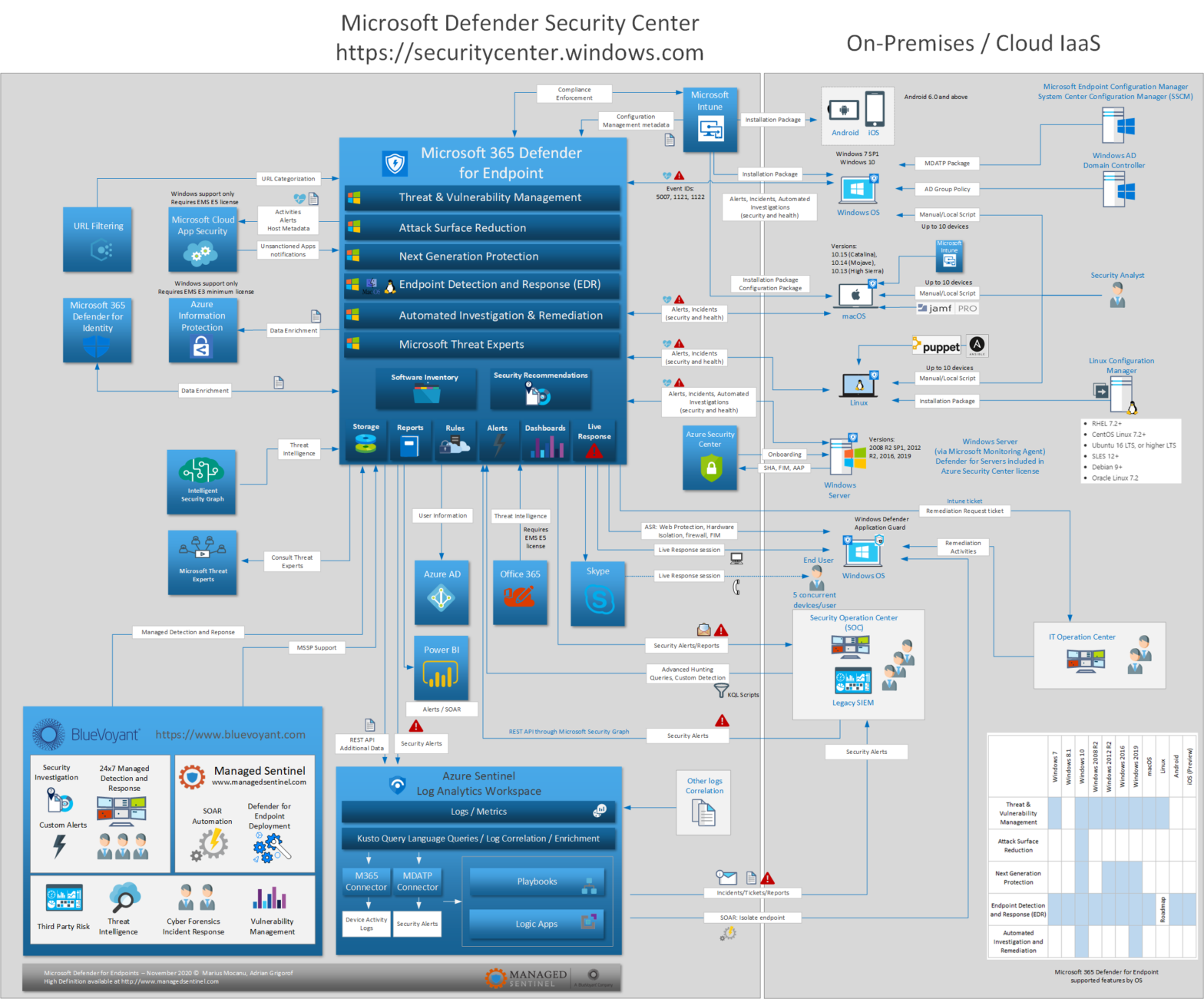
Microsoft 365 Defender for Endpoints
Formerly known as Defender ATP, Microsoft Defender for Endpoints is now a critical component of Microsoft XDR line of security controls. Defender for Endpoints is starting to go past its newly found fame as the “new kid on the block”, with a meteoric rise in Gartner’s Magic Quadrant for endpoint protection. It is now becoming […]
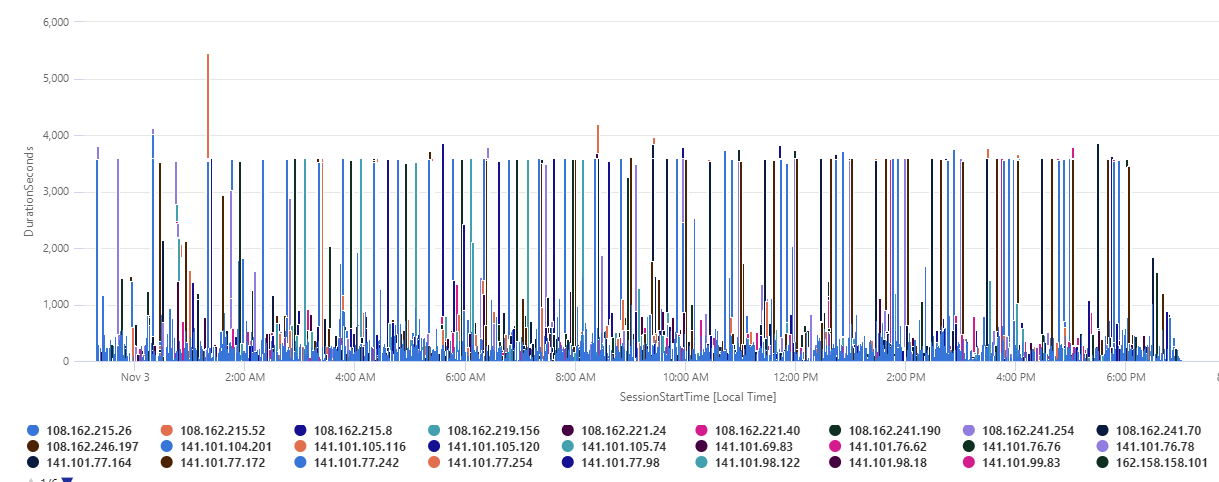
Using Kusto Query Language (KQL) in Azure Sentinel to calculate IIS session times
User sessions are an important aspect of identifying the behavior of web users. In many cases there is a lot of effort on ensuring that a user spends as much time visiting a website as it increase the chance of consuming the services offered by that particular website, be that advertising material, sales, etc. Onboarding […]