May 13, 2025
The Need for Custom SIEM Content
Picture this — your organization has not only deployed Microsoft Sentinel using best practices, but also has confidently answered questions on log sources, health monitoring, and automations that we discussed in this BlueVoyant blog. What’s next? It’s time to think about SIEM content. More specifically, custom SIEM content that goes beyond the out-of-the-box ones available […]
Read More Oct 4, 2024
Sentinel Phantom Fields: Understanding and Managing Inaccessible Data
Microsoft has transitioned to a DCR-based log ingestion and manual schema management for tables. Many organizations are adopting this modern approach to parse, filter, and enrich logs during ingestion. While effective, this system can incur unnecessary expenses if not used properly, leading to billable fields that remain inaccessible when querying events. We refer to these […]
Read More May 23, 2024
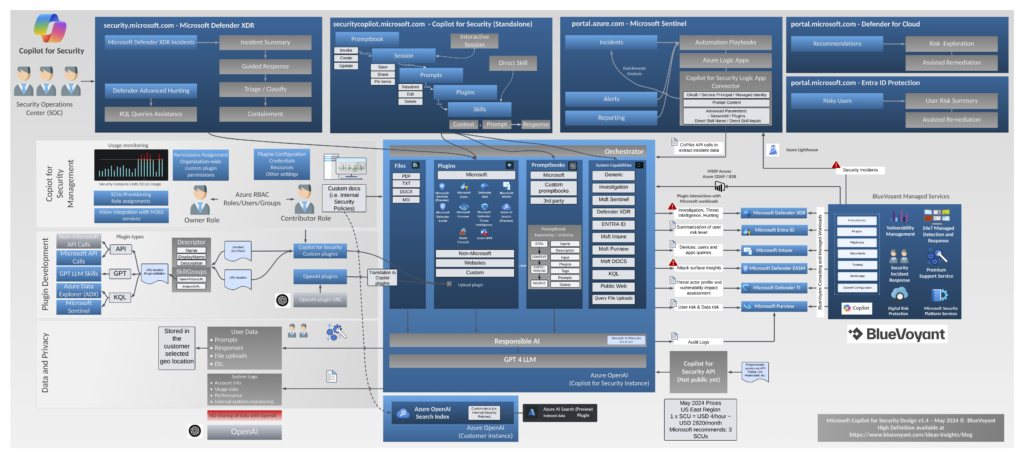
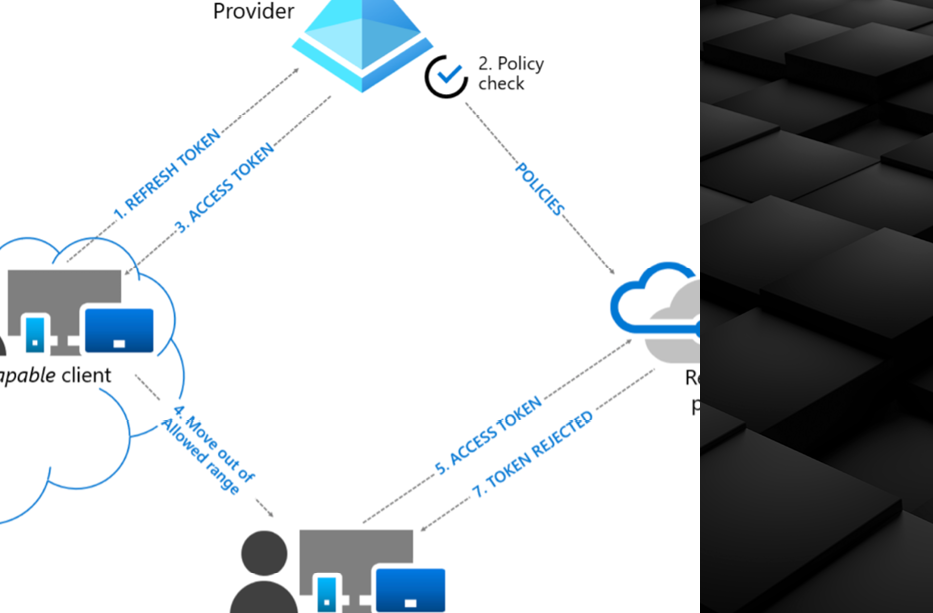
Microsoft Copilot for Security Design
We’re excited to continue our series of succinct visual guides with the release of our one-page diagram for Microsoft’s Copilot for Security – poised to revolutionize how Security Operations Center (SOC) analysts handle and analyze security events. With the ability to interpret complex, interrelated security events, generate sharp KQL scripts, integrate enrichments from both Microsoft […]
Read More Mar 13, 2024
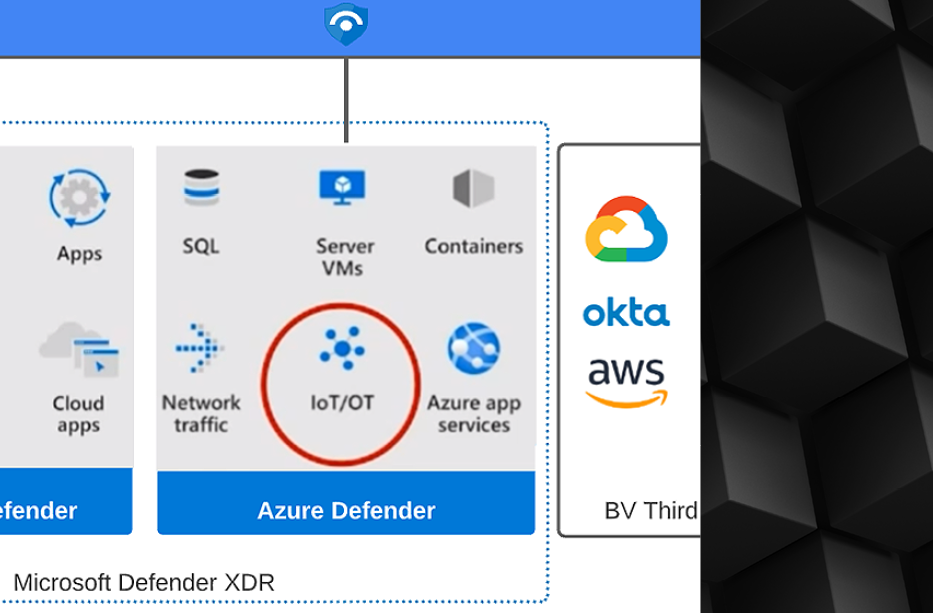
Defender for Cloud and Defender XDR Connectors in Sentinel
Over the past few weeks, Microsoft Defender for Cloud has received multiple updates. Microsoft has introduced a new tenant-level Defender for Cloud connector, replacing the old subscription-level one. Additionally, they have implemented a new functionality, allowing detections from Defender for Cloud to be integrated into Defender XDR, along with detections from other Defender solutions. There are […]
Read More Jan 9, 2024
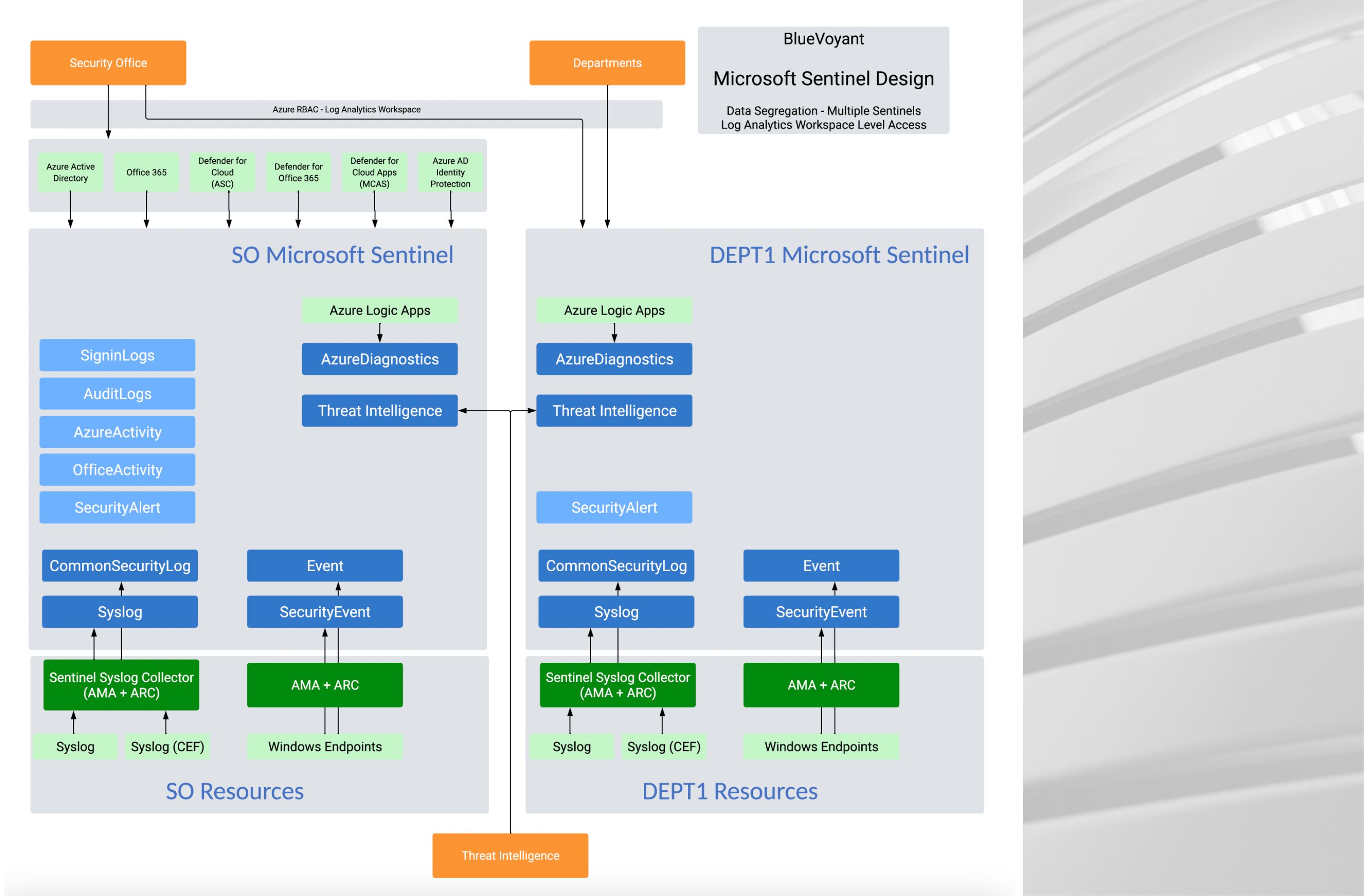
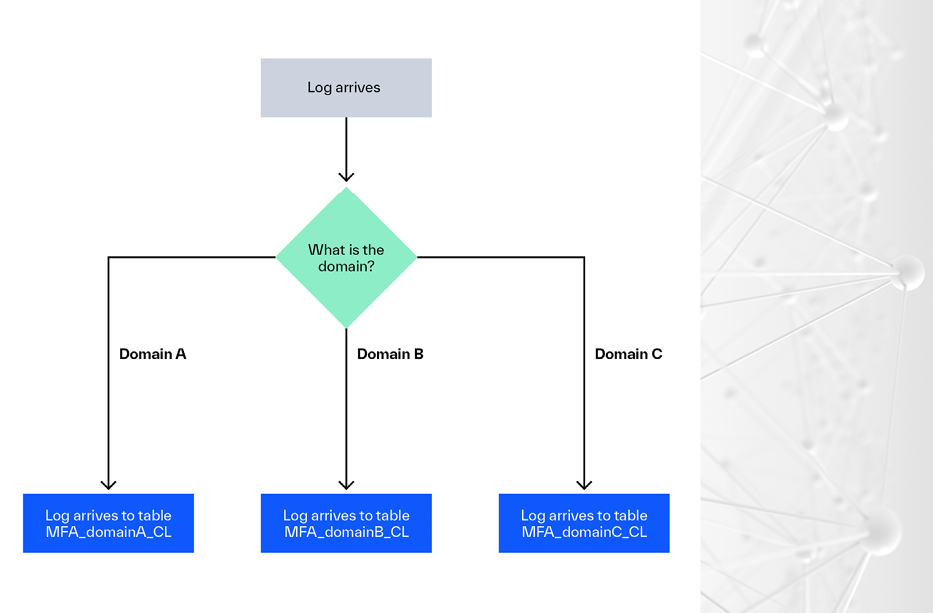
Microsoft Sentinel Data Segregation Options
So, you want to segregate your data in Sentinel? Well, you came to the right place! In this blog we are going to review four different ways that you can segregate data in Microsoft Sentinel. Keep in mind that there are pros and cons to every segregation option and that the best choice for your […]
Read More Jan 4, 2024
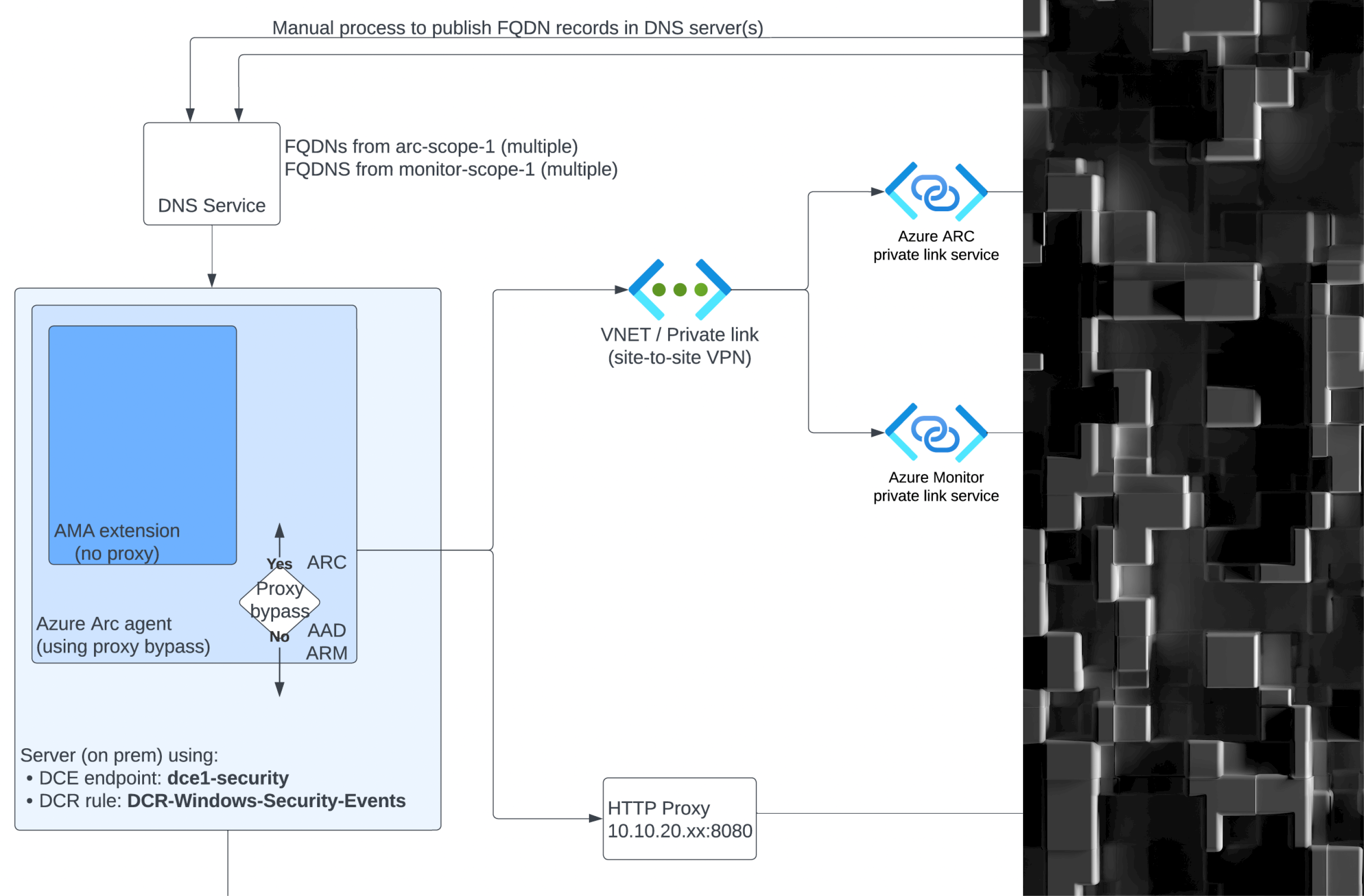
Complex Sentinel Deployments Using ARC and AMA Over Private Links and Private Endpoints
Large organizations sometimes opt for an architectural choice to use private links and private endpoints in the context of ingesting data from on-premise servers into Microsoft Sentinel. The typical reasons for this choice includes: Alignment with existing Azure architecture where solutions connecting datacenter to cloud such as ExpressRoute, or Azure VPN gateways are already adopted […]
Read More Oct 2, 2023
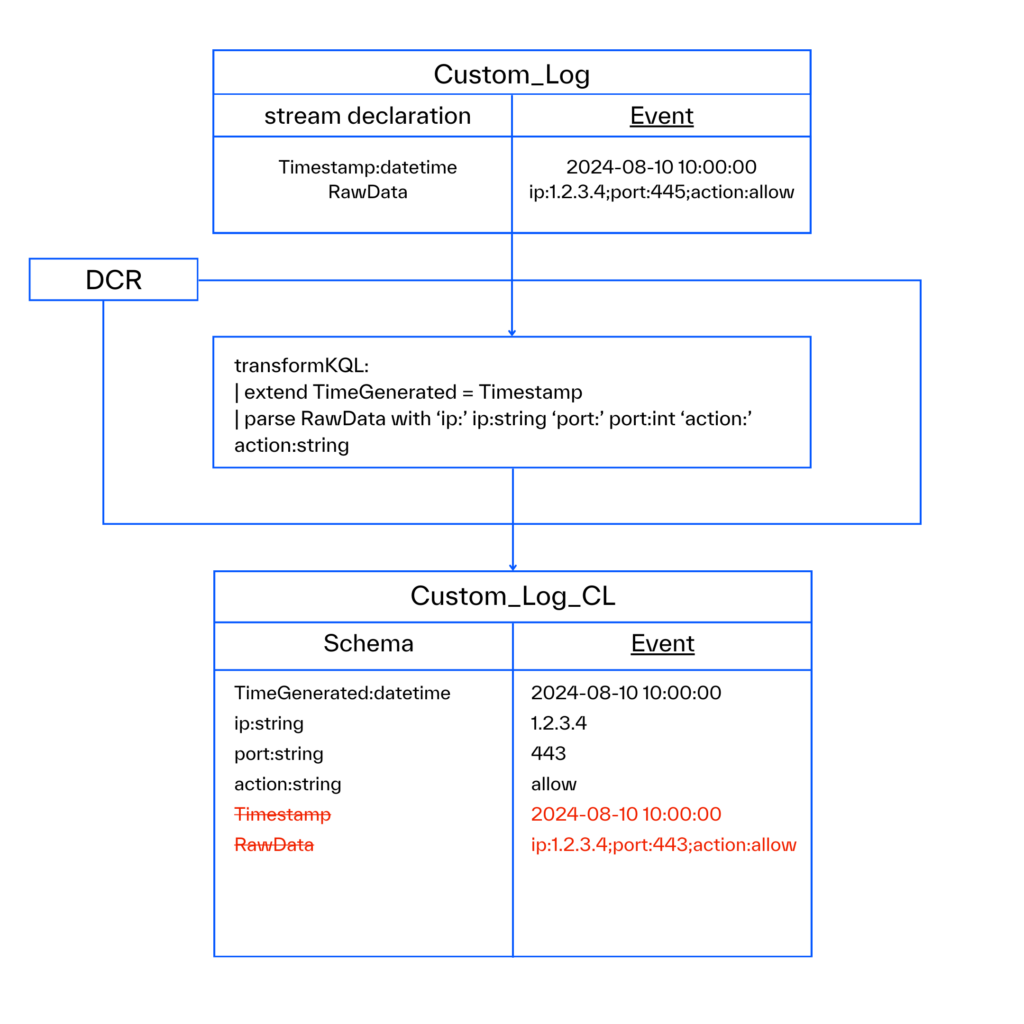
Log Splitting with Data Collection Rules
In a recent article, Microsoft discussed log splitting in Data Collection Rules (DCRs), also known as Multi-Destination Data Collection Rules. Microsoft mentioned a few uses for this capability. I’ve worked with numerous clients in the past who had certain needs that log splitting would have made much simpler to fulfill. In this blog post, I’ll […]
Read More Sep 18, 2023
From Noise to Action: Analyzing Activity Alerts and Preventing Genuine Threats with Defender for Cloud Apps
If you worked in a SOC, you know that during an analysis, correlating sessions to identify malicious activity or compromise is necessary, yet hard or impossible to perform, based on the available logs from activity-based alerts from Defender for Cloud Apps. In this blog post, we will go over the following topics: What are the […]
Read More Aug 31, 2023
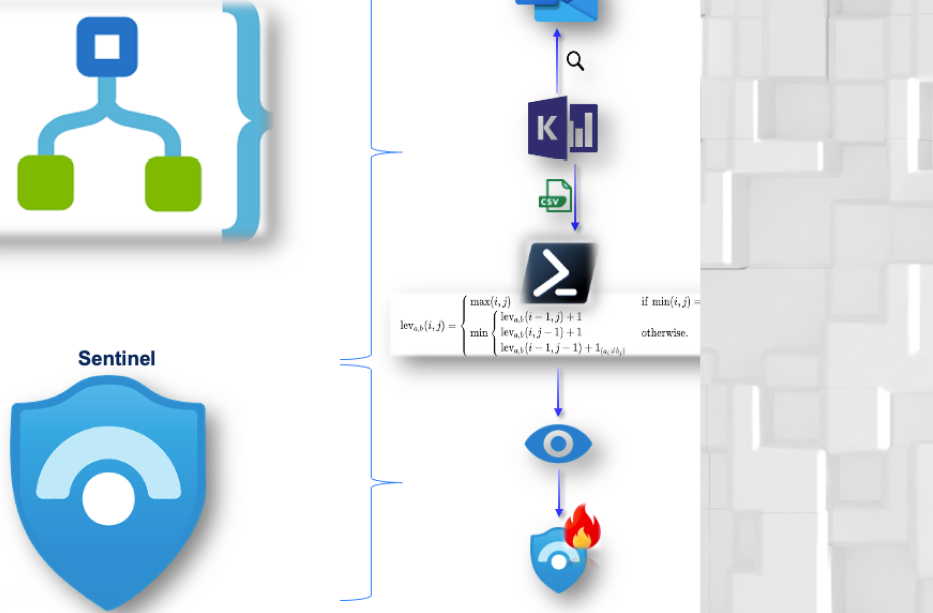
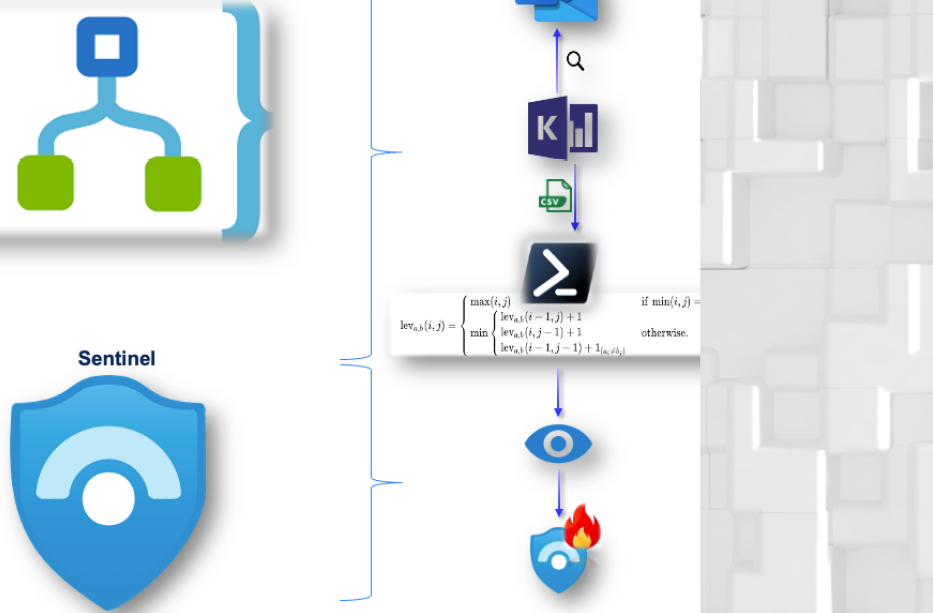
Maximizing the Value of Azure Automation for SOCs
A BlueVoyant Custom Levenshtein Detection What Does This Detection Mitigate? This use case has been designed to capture email spoofing attempts from an external attacker where the attacker impersonates an internal user or trusted supplier. As domain verification is not built into the Simple Mail Transfer Protocol (SMTP), attackers can counterfeit email addresses with the […]
Read More Jul 25, 2023
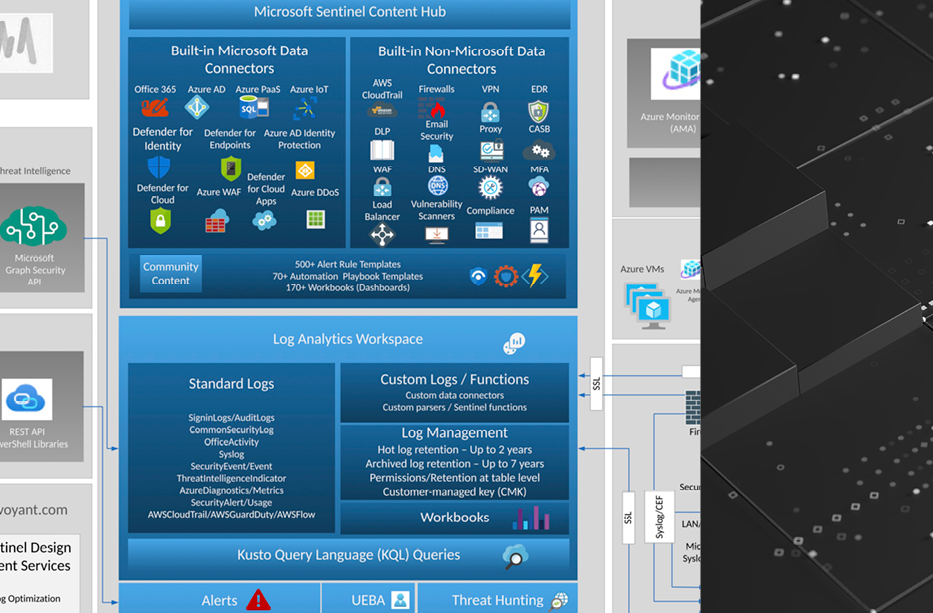
Microsoft Sentinel Design – Updated One-Page Diagram
Microsoft Sentinel has introduced a significant number of new features and improvement of existing ones since our last diagram update. Some notable ones are increased incident management options, addition of large number of solutions including data connectors, detection rules and workbooks, content management options such as Workspace Manager, centralized data collection rules via the Azure […]
Read More Nov 29, 2021
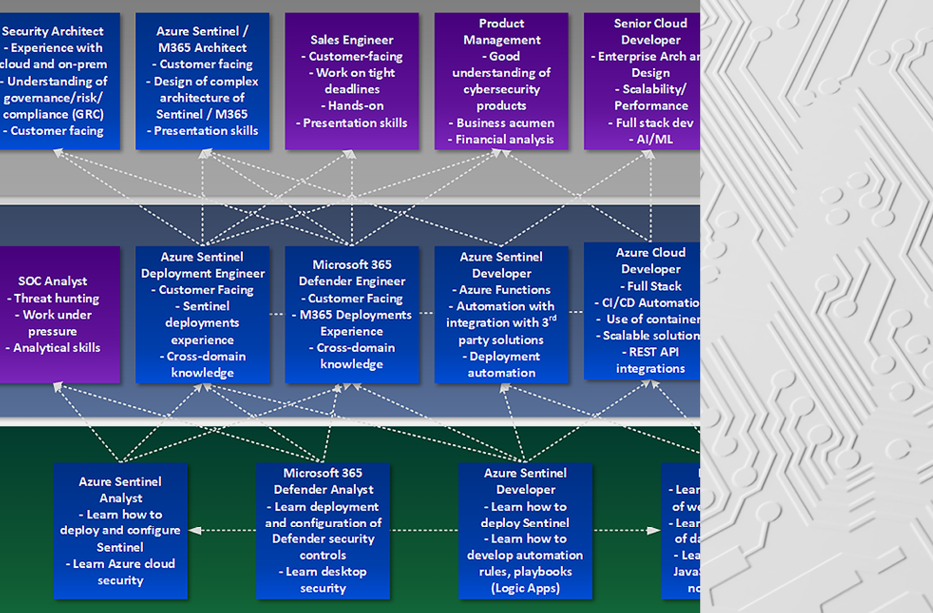
Join Our Team: BlueVoyant – Microsoft Security Consulting Potential Career Paths
In the context of a highly pace of change in technology and paradigm shifts on an almost daily basis, BlueVoyant is always looking for talented people who are flexible, willing to tackle new technologies, explore, get their hands on the latest cybersecurity tools, and literally grow with us. It is not an easy task, but […]
Read More Sep 29, 2021
Defender for IoT Raw Log Integration into Sentinel
Microsoft Defender for IoT sensors have limited out-of-the-box capabilities to integrate their data into Azure Sentinel. Today the sensor platform supports only sending alerts to Sentinel, which is limiting since a modern SOC must have the ability to correlate any relevant sensor data that occurred around the alerts with other sources to form a complete […]
Read More