Over the past few weeks, Microsoft Defender for Cloud has received multiple updates. Microsoft has introduced a new tenant-level Defender for Cloud connector, replacing the old subscription-level one. Additionally, they have implemented a new functionality, allowing detections from Defender for Cloud to be integrated into Defender XDR, along with detections from other Defender solutions. There are […]
Results for ""
Brian Rowe
Security Architect
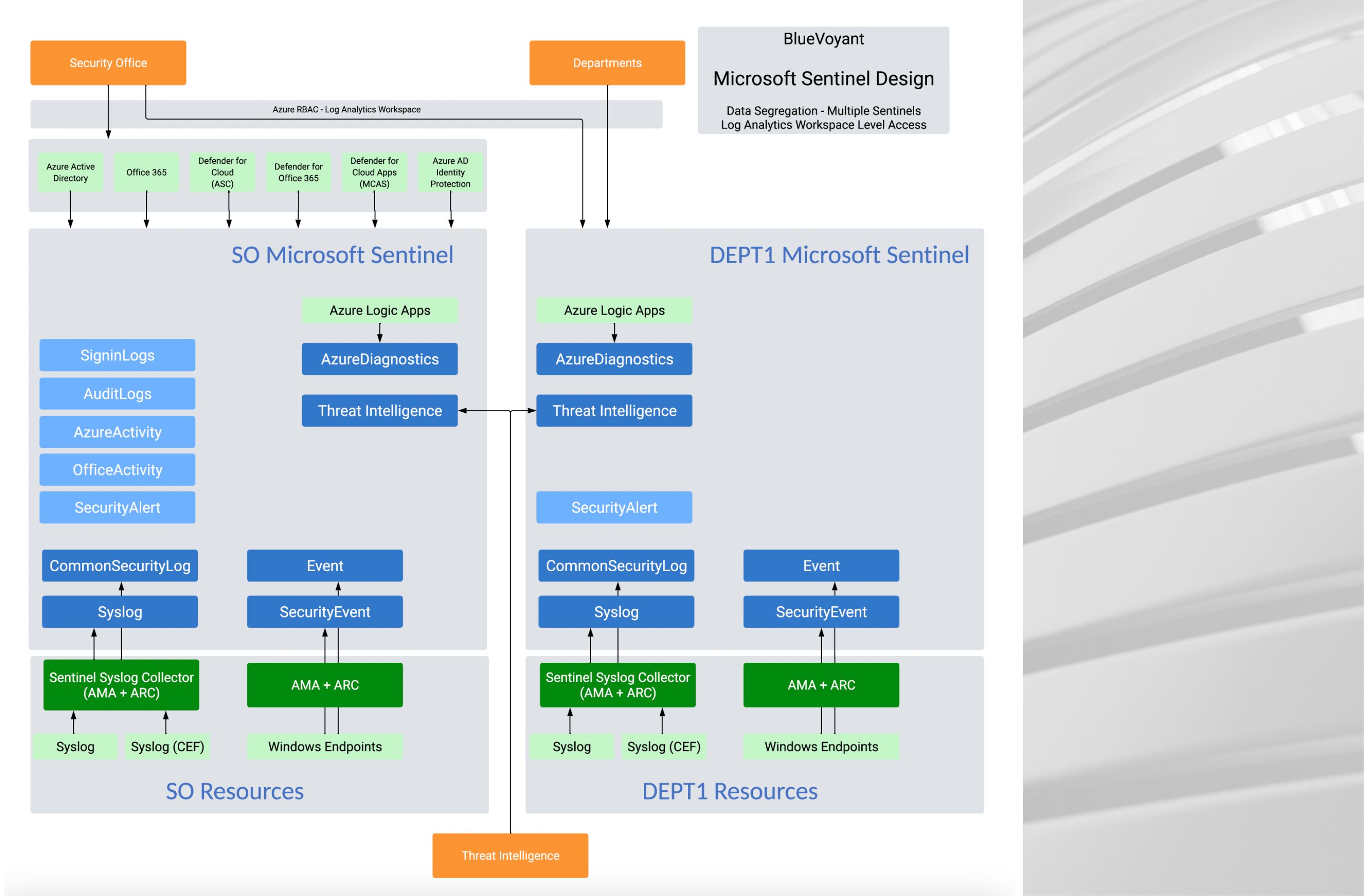
Microsoft Sentinel Data Segregation Options
So, you want to segregate your data in Sentinel? Well, you came to the right place! In this blog we are going to review four different ways that you can segregate data in Microsoft Sentinel. Keep in mind that there are pros and cons to every segregation option and that the best choice for your […]
George Stefan
Cloud Architect
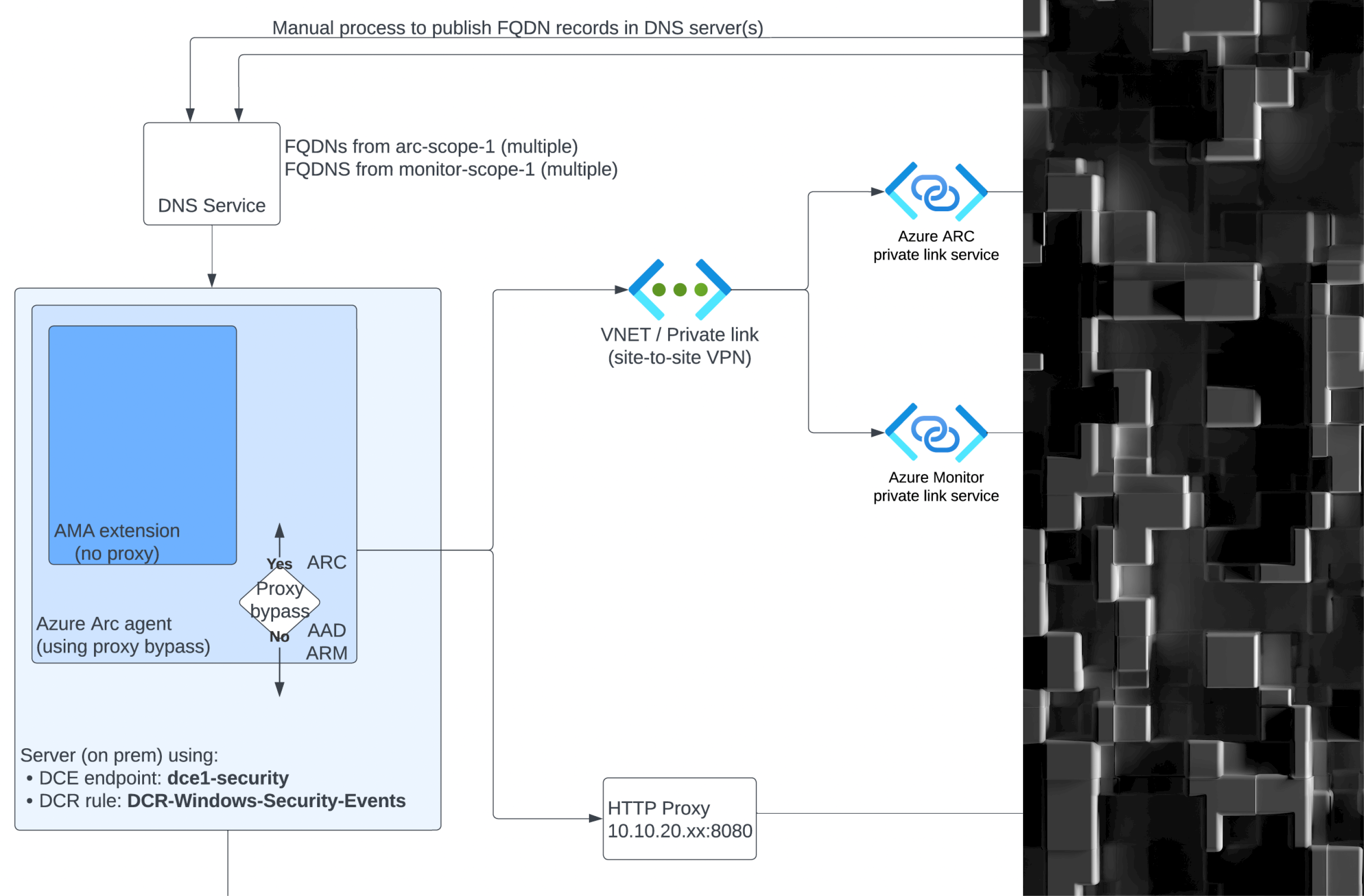
Complex Sentinel Deployments Using ARC and AMA Over Private Links and Private Endpoints
Large organizations sometimes opt for an architectural choice to use private links and private endpoints in the context of ingesting data from on-premise servers into Microsoft Sentinel. The typical reasons for this choice includes: Alignment with existing Azure architecture where solutions connecting datacenter to cloud such as ExpressRoute, or Azure VPN gateways are already adopted […]
Sándor Tőkési
Senior Sentinel Engineer
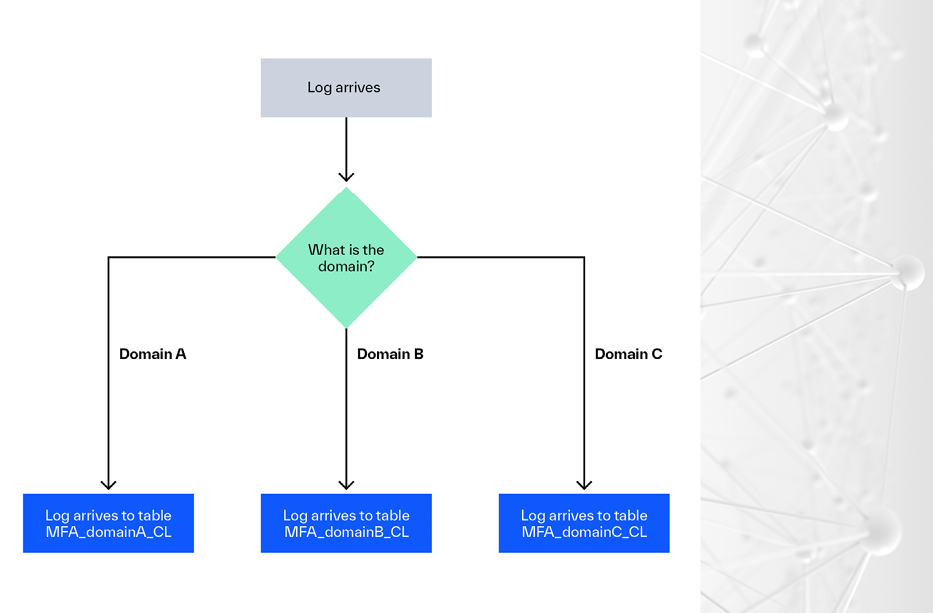
Log Splitting with Data Collection Rules
In a recent article, Microsoft discussed log splitting in Data Collection Rules (DCRs), also known as Multi-Destination Data Collection Rules. Microsoft mentioned a few uses for this capability. I’ve worked with numerous clients in the past who had certain needs that log splitting would have made much simpler to fulfill. In this blog post, I’ll […]
Gábor Szekeres
Microsoft Cloud Security Specialist
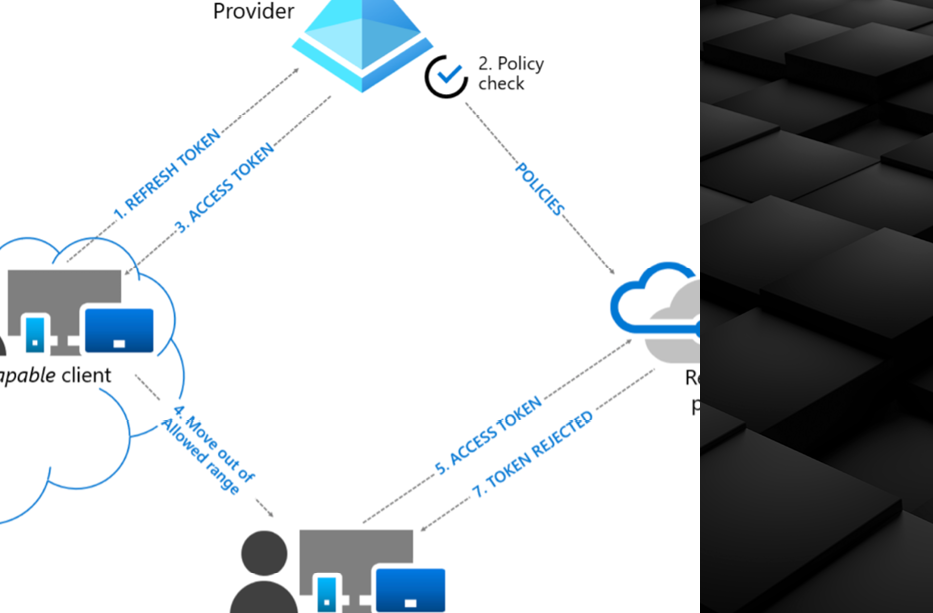
From Noise to Action: Analyzing Activity Alerts and Preventing Genuine Threats with Defender for Cloud Apps
If you worked in a SOC, you know that during an analysis, correlating sessions to identify malicious activity or compromise is necessary, yet hard or impossible to perform, based on the available logs from activity-based alerts from Defender for Cloud Apps. In this blog post, we will go over the following topics: What are the […]
Nick Wade
Microsoft Sentinel SIEM Engineer