Picture this — your organization has not only deployed Microsoft Sentinel using best practices, but also has confidently answered questions on log sources, health monitoring, and automations that we discussed in this BlueVoyant blog. What’s next? It’s time to think about SIEM content.
More specifically, custom SIEM content that goes beyond the out-of-the-box ones available from Microsoft to ensure your organization is maximizing their Microsoft investment. Ideally, you want to augment Microsoft Sentinel content with a solid repository of best-in-class content, along with unique ones that are tailor-made for your organizational needs. If you do not have a strong library in-house or from your MDR provider, then BlueVoyant’s Continous Optimization for Micosoft Security (COMS) can help.
Why use BlueVoyant COMS? This solution provides managed SIEM content using a repository of best-in-class use cases, along with those that optimize content hub detection rules. We have an in-house content development team, and we often create custom content for our enterprise customers.
Let’s dig a bit deeper into what COMS offers.
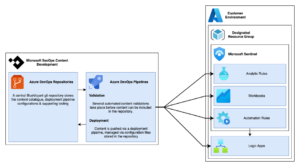
COMS Provides Optimized Content Hub Detection Rules
Improvements include query performance optimization, ASIM translations & metadata updates
let lookback = 1h;
let latency = 1h;
let MultifactorDeclined = (tableName:string){
table(tableName)
| where TimeGenerated >= ago(lookback + latency)
| where ResultType == 500121
| where Status has "MFA Denied; user declined the authentication"
or Status has "MFA denied; Phone App Reported Fraud"
| extend ConditionalAccessPolicies=parse_json(ConditionalAccessPolicies)
, DeviceDetail=parse_json(DeviceDetail)
, LocationDetails=parse_json(LocationDetails)
, MfaDetail=parse_json(MfaDetail)
, Status=parse_json(Status)
| extend Details=Status.additionalDetails
| extend Name = tostring(split(UserPrincipalName,'@',0)[0]), UPNSuffix = tostring(split(UserPrincipalName,'@',1)[0])
};
//
union MultifactorDeclined("SigninLogs")
, MultifactorDeclined("AADNonInteractiveUserSignInLogs")
| join kind=inner (
BehaviorAnalytics
| where TimeGenerated >= ago(lookback)
| where ActionType =~ 'User did not pass the MFA challenge'
| where ActivityInsights.UnusualNumberOfAADConditionalAccessFailures == True
and (
ActivityInsights.FirstTimeUserAccessedResource == True
or ActivityInsights.FirstTimeUserUsedApp == True
or ActivityInsights.ResourceUncommonlyAccessedByUser == True
)
| extend AppDisplayName = ActivityInsights.App
| project ActivityInsights, InvestigationPriority, UserPrincipalName, TimeGenerated, AppDisplayName, IPAddress = SourceIPAddress
| summarize UEBATime = max(TimeGenerated),
InvestigationPriority = sum(InvestigationPriority),
ActivityInsights = make_set(ActivityInsights)
by UserPrincipalName = tolower(UserPrincipalName), tostring(AppDisplayName), IPAddress
) on UserPrincipalName, AppDisplayName, IPAddress
| where UEBATime >= TimeGenerated - 15m
| summarize count(), arg_max(TimeGenerated, *) by UserPrincipalName, IPAddress, Location, AppDisplayName, ClientAppUsed
BlueVoyant maximize the use of Sentinel UEBA as detailed on lines 20 – 36. This ensures the Rule only fires where UEBA has confirmed an unusual number of AAD Conditional Access Failures and it is the first time the resource is being accessed or is uncommonly accessed by the respective User.
COMS Uses Fully In-house Developed Content
Our team of detection engineers have built a large amount of detection rules to help you achieve balanced MITRE ATT&CK coverage & detect attacks as soon as possible and support a wider array of log sources. This provides a layer on top of the above bucket with full alignment to Microsoft schemas and functions.
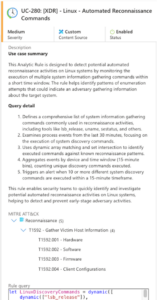
As with all the Analytical Rules that BlueVoyant deploy, detailed descriptions are provided. In this example, we’ve provided this rather than the KQL — as it’s so descriptive, you could write this yourself or reach out if you need a hand.
COMS Creates Enterprise Customer Requested Content
Complex use cases that arose from customer requests which have been generalized as much as possible and can provide great value to all businesses. We have extensive experience with migrating use cases from legacy SIEMs and translating their logic to Sentinel. Just like the below example:
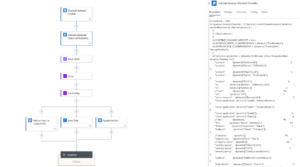
We’ve taken great pride in re-implementing under the hood functions in other SIEM tools, such as Shannon Entropy, Levenshtein Distance algorithm and Bayesian calculation, to transform into KQL. This is a Bayesian Incident scoring automation to enable your SOC to prioritize and manage Incidents on any content that is well Entity mapped. Just like ours.
All of our content has proven itself at large enterprise customers and is aligned to Microsoft’s best-practices; we aim to maximize the use of the ASIM normalization schemas, for example. Doing so provides you with instant wide coverage of your logs, and the ability to correlate & track attacks across your various data sources. And we do this in the most optimal way. For example, we push our finely tuned Windows Security Event Data Collector Rule to only ingest EventIDs required for Analytical Rules or part of the Microsoft ‘Minimal Set’
Another best practice we adhere to is that of mapping entities using strong identifiers where possible. This makes investigation easier by surfacing involved IPs, users, & hosts with full enrichment, but also enables the use of the investigation graph view & further correlation in the Microsoft Defender XDR stack.
Additionally, we employ several quality validation stages before we consider our content ready to deploy. Our analytic rules will always include the following, ensured by way of automated checks & mandatory peer reviews:
- A mapping to the relevant MITRE ATT&CK tactics & techniques
- A detailed description consisting of:
- Details of the activity that the use case captures
- A breakdown of the query’s logic
- In-depth information regarding MITRE ATT&CK mapping
- Additional considerations for investigation & remediation
- Strongly mapped entities for enhanced aggregation & investigation features
- Well-informed aggregation policies
- Optimized query frequency & lookback periods
Our quality assurances extend past detections, and into automations & workbook reporting as well; Every single piece of content that is included in our repository is validated by at least 2 engineers for value, correctness, quality & maintainability.
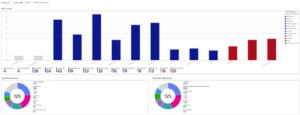
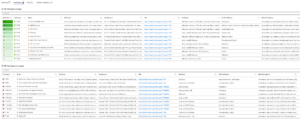
An example on one of our Workbooks captured in a demonstration workspace. This will provide your Executives with complete situational awareness of your MITRE ATT&CK coverage and the techniques that are missing controls.
Learn more about Continuous Optimization for Microsoft Security
