

Are you maximizing your use of Microsoft’s security capabilities? If not, we can help.
With BlueVoyant’s Microsoft security consulting and deployment services, you don’t need to be an expert to take your security and compliance posture to the next level. Our Accelerator services are designed to get you up and running quickly and to maximize your investment in Microsoft Azure Sentinel and 365 Defender security technologies.
How do I get started?
Microsoft Security Accelerators from Managed Sentinel
Pick one or both of our Accelerator services below. We will perform detailed analysis of your environment(s) and provide actionable security insights. What’s included: A detailed assessment of your risks, guidance on how best to leverage Microsoft-powered solutions and/or deployment & configuration assistance based on your unique situation.
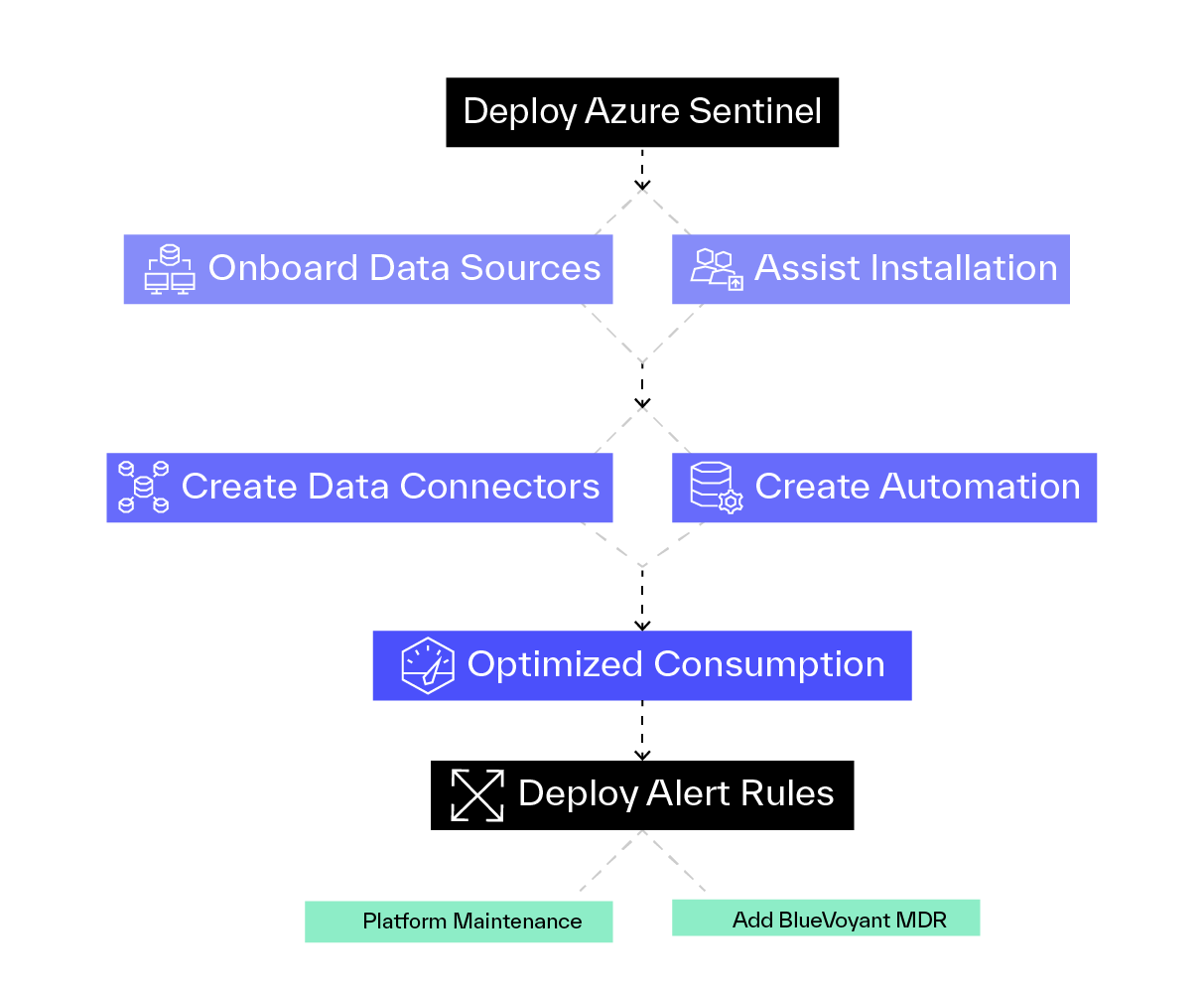
Azure Sentinel Accelerator
- Deploy Azure Sentinel in your Azure subscription
- Assist with the installation of Azure Syslog/CEF collector
- Onboard all Microsoft native data sources
- Onboard and tune 3rd party data sources
- Create custom data connectors (as required)
- Create SOAR automation playbooks
- Optimize your Azure consumption based on security and intelligence value vs. consumption costs
- Deploy BlueVoyant Sentinel Alert rules
Optional
- Add ongoing platform maintenance service
- Add BlueVoyant MDR
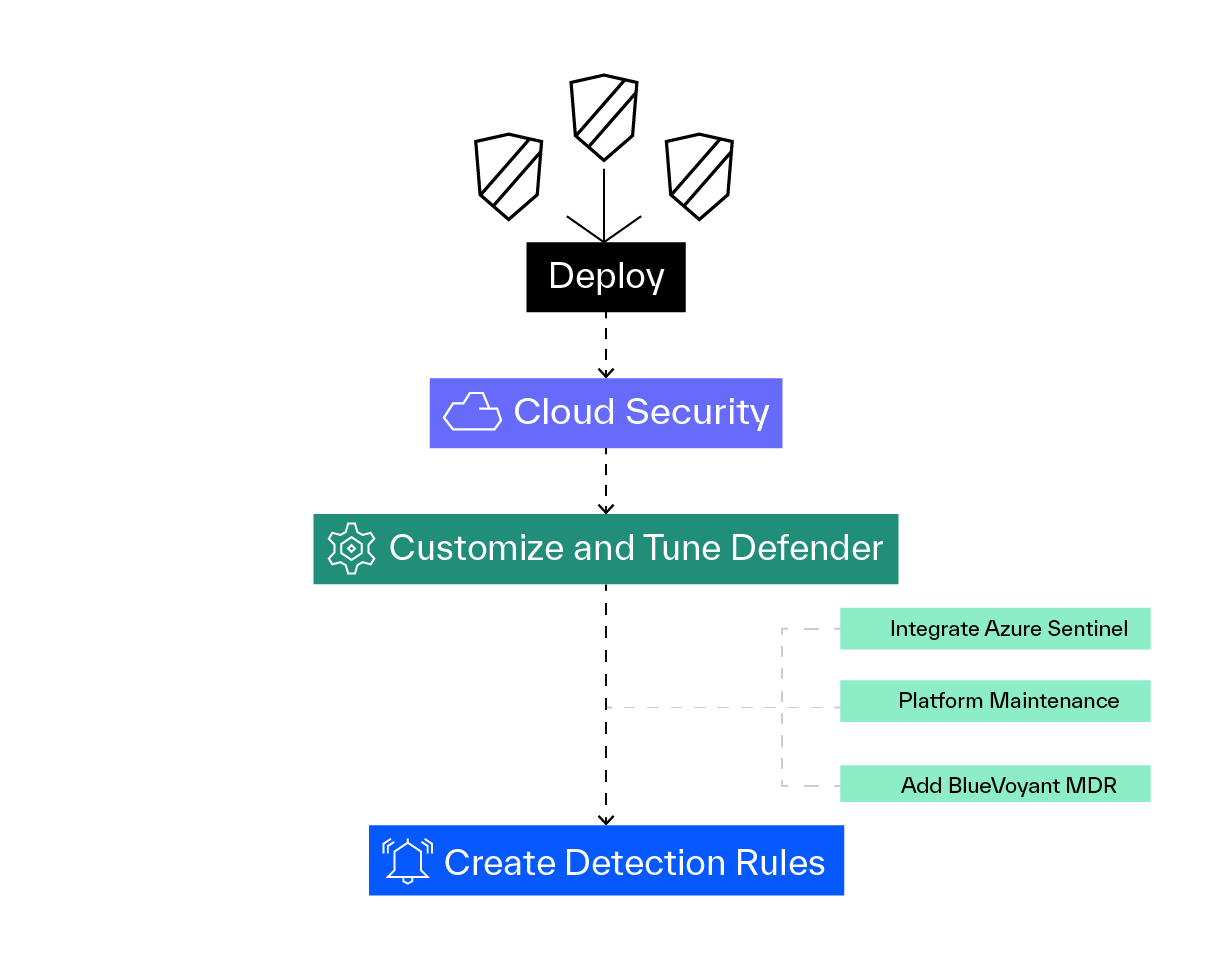
365 Defender Accelerator
- Deploy
- Defender for Endpoint
- Defender for Identity
- Defender for Office 365
- Microsoft Cloud App Security
- Customize and tune Defender policies to your organization needs
- Create detection rules specific to your organization
Optional
- Integrate Azure Sentinel
- Add ongoing platform maintenance service
- Add BlueVoyant MDR

Why Managed Sentinel?
When it comes to security, you need an experienced partner.
Managed Sentinel offers a broad portfolio of consulting, deployment & managed security services focused on leveraging the power of Microsoft security technologies.
