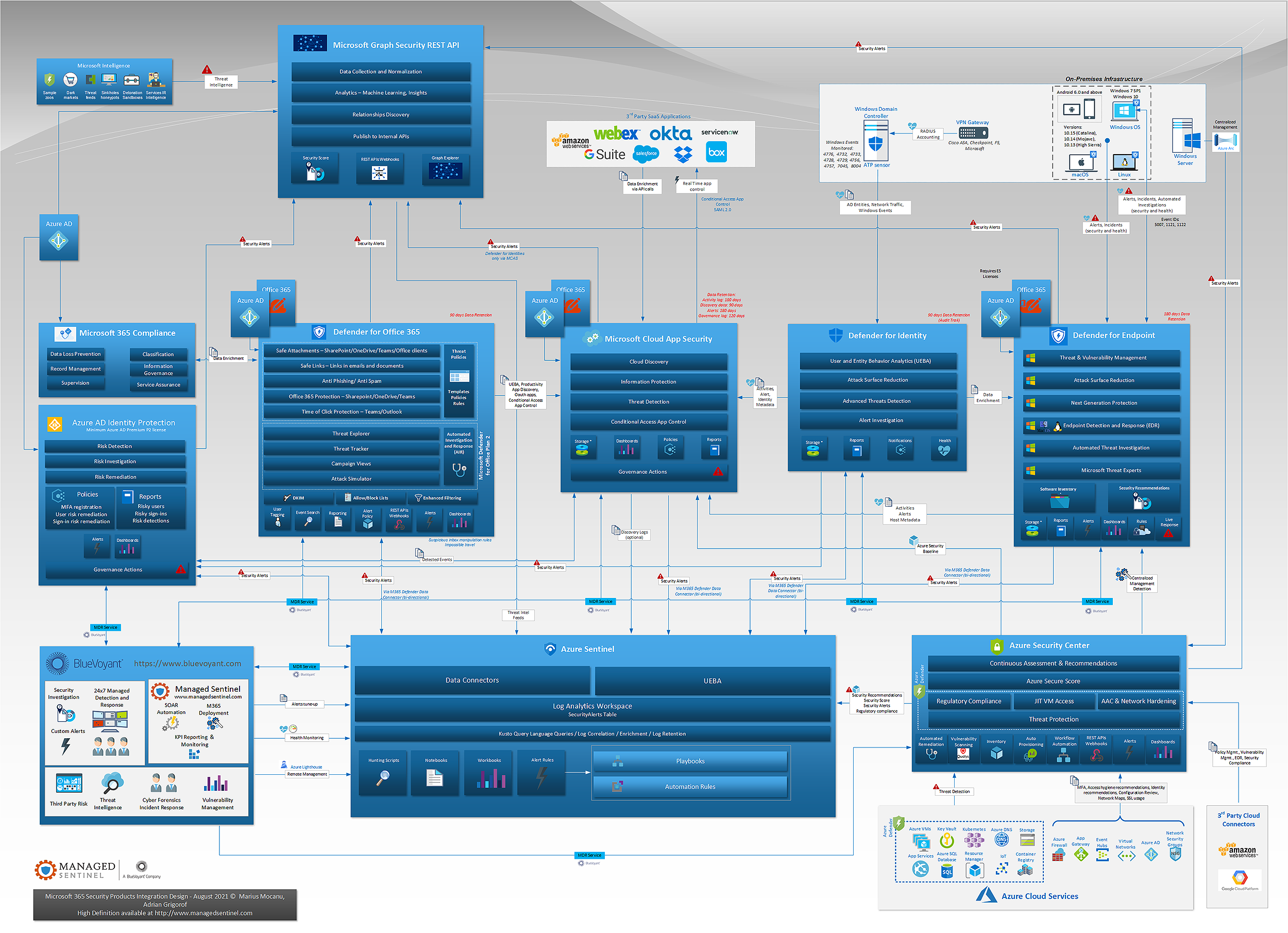
In the past we have published individual diagrams for a number of Microsoft cloud security solutions, but in the end we always intended to have the larger picture that can provide analysts with a visual understanding on what type of data is exchanged between various Microsoft security controls and how that data is used to enrich detections and provide additional context. This would allow for better understanding of the alerts generated by each solution, identify additional log sources that would complement them, and potential gaps in the overall visibility.
This diagram required a bit of effort in consolidating the large numbers of connections and signal exchange pipelines between the Microsoft security controls; we have omitted some less relevant connections in order to optimize the understanding of the main ones.
Azure Active Directory and Office 365 emerged as critical log sources – and rightly so, as almost any attack eventually will leave footprints in one of these solutions, especially for some of the most destructive attacks such as ransomware delivered via emails. Microsoft Graph, through its Security REST API acts as versatile way of sharing signals between security controls and in itself can be used as a good source for custom detection rules.
We can see that we have no more than two degrees of separation between almost any log source in a typical hybrid infrastructure, with applications hosted in public cloud, SaaS or on-premises.
The importance of governance, risk and compliance is reflecting more and more in the technical controls themselves, with solutions such as Microsoft 365 Compliance and Security Center interacting directly with the other products in order to both assess the compliance status and even remediate resources out of compliance.
Almost all the products have SOAR capabilities though, ideally, one would use the single pane of glass offered by Azure Sentinel for alert rules, dashboards and automation tasks.
Marius Mocanu serves as Managed Sentinel’s CEO and Adrian Grigorof is its CTO.
Be sure to download the high-resolution PDF.