The Office 365 activity log connector provides insight into ongoing O365 user activities. By configuring Office 365 Connector in Azure Sentinel you will get details of operations such as file downloads, access requests sent, changes to group events, set-Mailbox and details of the user who performed the actions.
This information will be visible in Azure Sentinel Dashboards and will allow your security administrators to create alerts and improve the security investigation process.
This document is a step-by-step guide of how to configure the Office 365 Connector in Azure Sentinel.
Prerequisites
- A global administrator or security administrator account in Azure Sentinel workspace
- Access to port TCP/4433 (web traffic) to Office 365 from the computer from where the change will be done.
- Ability to run PowerShell as local administrator
- Administrator account in Office 365
Activities
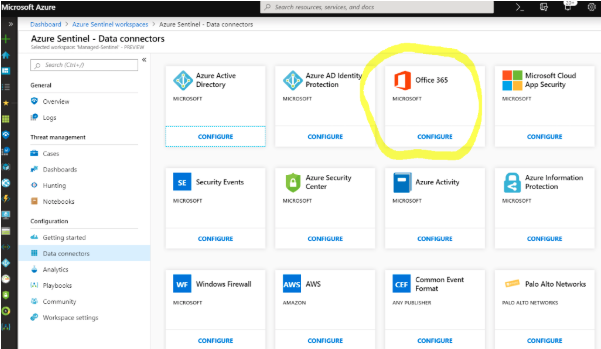
1. Azure Sentinel, select Data connectors and then click the Office 365 Configure tile:
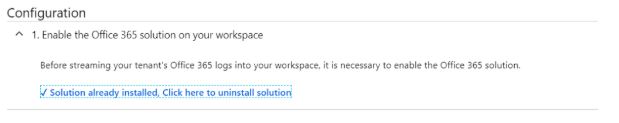
2. Under Connection use the Enable button to enable the Office 365 solution:
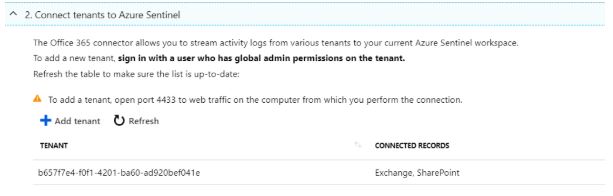
3. Office 365 enables you to stream data from multiple tenants to Azure Sentinel. In the Connect tenants section, click Add tenant. In the Active Directory pop-up menu authenticate with a global administrator account to connect to Azure Sentinel and provide permissions to read its logs. Repeat the operation for any additional tenants that you want to monitor.
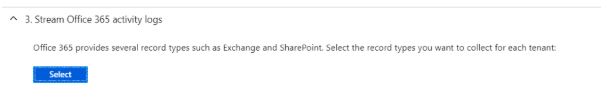
4. Under Stream Office 365 activity logs, click Select to choose which log types you want to stream to Azure Sentinel. Select Exchange and SharePoint.
5. Click Apply changes.
6. At this point you will need to enable audit log recording for Office 365. Login to Office 365 Security and Compliance Center with admin privileges.
7. In the Security & Compliance Center, go to Search & investigation > Audit log search
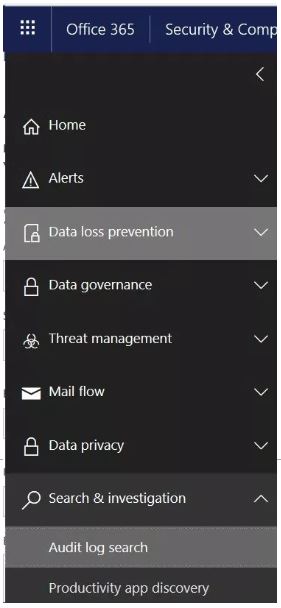
8. Click Start recording user and admin activities
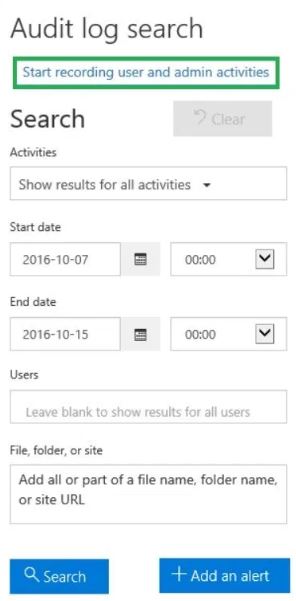
9. A dialog box will be displayed saying that “User and admin activity in your organization will be recorded to the Office 365 audit log”. Click Turn on.
Alternatively, you can turn on the audit log recording in Office 365 using PowerShell. Open the Windows PowerShell and execute the following commands if the Microsoft Online Services Sign-in Assistant has been installed:
C:> Import-Module MSOnline
Execute the following command:
C:> $LiveCred = Get-Credential
Enter the admin credentials in the pop-up dialog. Execute the following command:
C:> $Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell/ -Credential $LiveCred -Authentication Basic –AllowRedirection
Execute the following command:
C:> Import-PSSession $Session
You are connected now. If the Microsoft Online Services Sign-in Assistant has been installed, execute the following commands:
C:> Connect-MsolService –Credential $LiveCred
To enable auditing, execute the following command:
C:> Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
10. Configuration is completed. To use the relevant schema in Log Analytics for the Office 365 logs, search for OfficeActivity.
Please note that it can take up to 24 hours for Office 365 audit logs to be ingested in the Azure Log Analytics and to become visible in Azure Sentinel.
Below is a sample of standard Office 365 Azure Sentinel Dashboard. Data and graphs started to populate only a few days after the Office 365 Azure Sentinel connector was configured:

