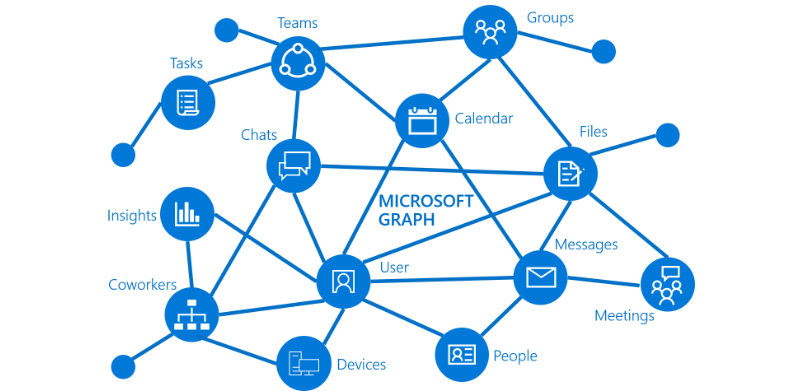
Microsoft Graph, the Security component was born as a way to represent the threat intelligence information in a form that is closer to the way they attackers approach their targets, as a graph of interconnected systems, with complex relationships between themselves and 3rd party entities. Inside the graph, Microsoft is using their substantial analytical power to aggregate, normalize and feed this data to consumers that have the potential not just to use it in their detections, but to enrich it further.
Each of the entities part of the Microsoft Graph can and do have security-related context. This context is continuously rebuilt through the integration with various Microsoft security controls, Microsoft security intelligence and 3rd party security providers. The results are accessible through the Microsoft Graph Security API that works both ways, allowing consumers to retrieve data as well as update it with additional content. Those interested in exploring it interactively can visit Microsoft’s Graph Explorer and select some of the security-related examples, such as security alerts from various sources (the right permissions are required in order to retrieve the data).
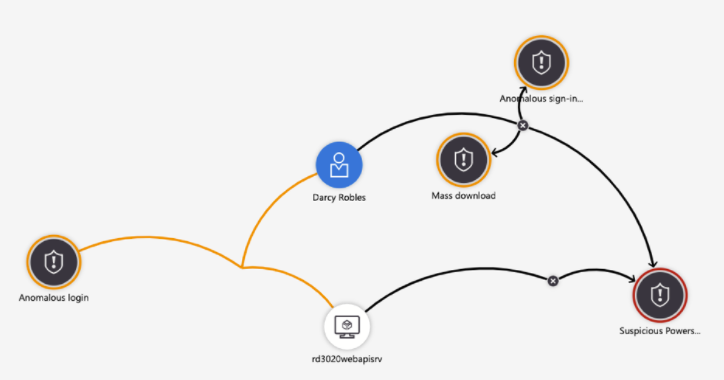
The concept of graph is also reflected in Azure Sentinel investigation, with the various types of entities (hosts, IP addresses, accounts, URLs and file hashes) can paint a more relevant picture on how different alerts relate to each other. Different entities are being added by Microsoft so in time it will become an interesting tool to investigate events.
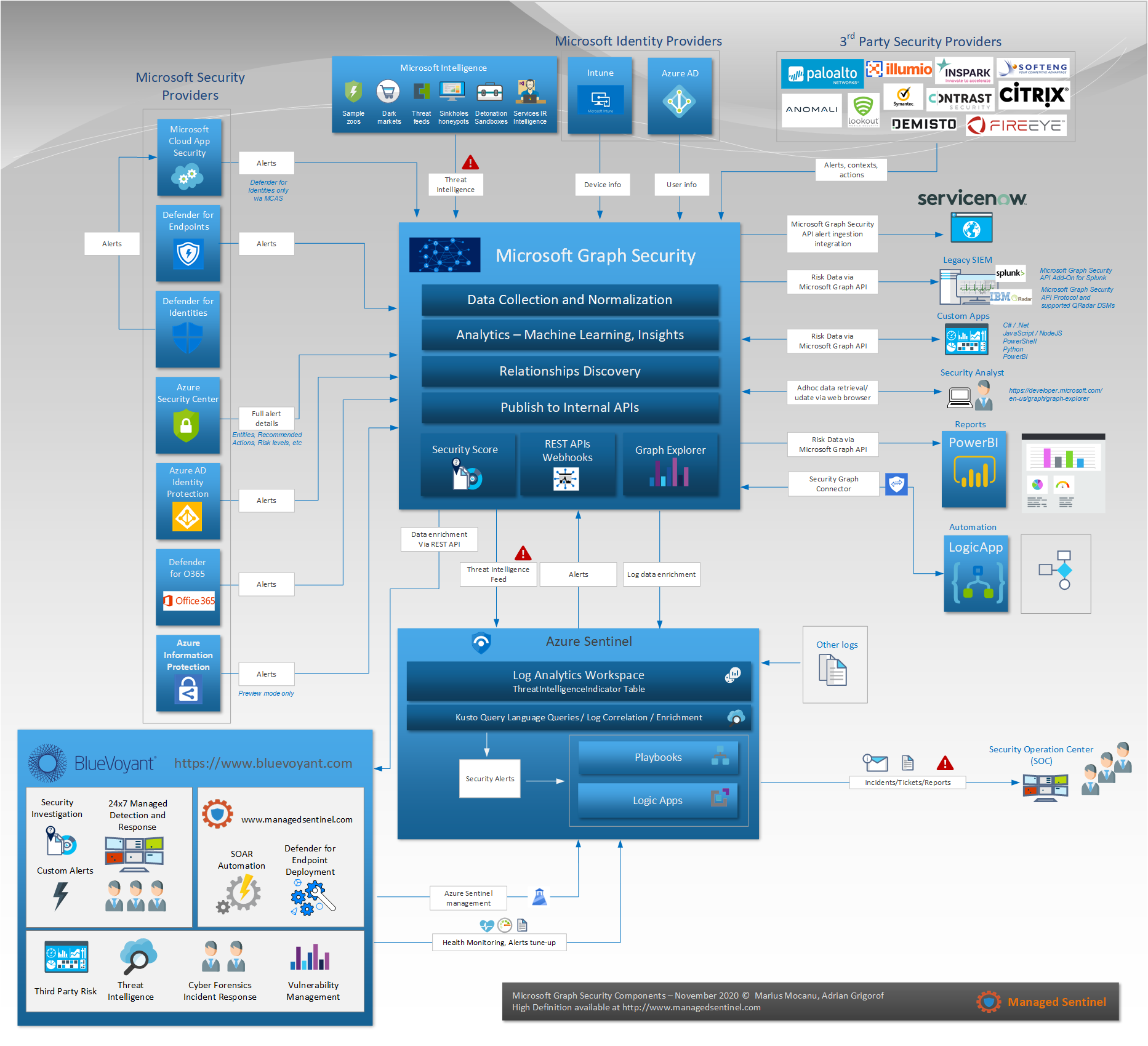
The diagram below represents our effort to provide a one-page, visual representation of how various systems integrate with the Microsoft Graph Security as well as ways to consume the data available through Microsoft security solutions, 3rd party apps or even in-house, custom developed services.
Contact us for full walk-through of this diagram and a review of Microsoft Graph Security integration with the overall Microsoft security stack.
In addition to the information available through Microsoft Graph Security API, during the incident investigation process part of its MDR service, BlueVoyant is leveraging its substantial threat intel, collected through its dedicated services. These go beyond the traditional threat feeds and can be provided as independent services to cover third-party risk and unconventional attack vectors. See our comprehensive list of threat intelligence services.