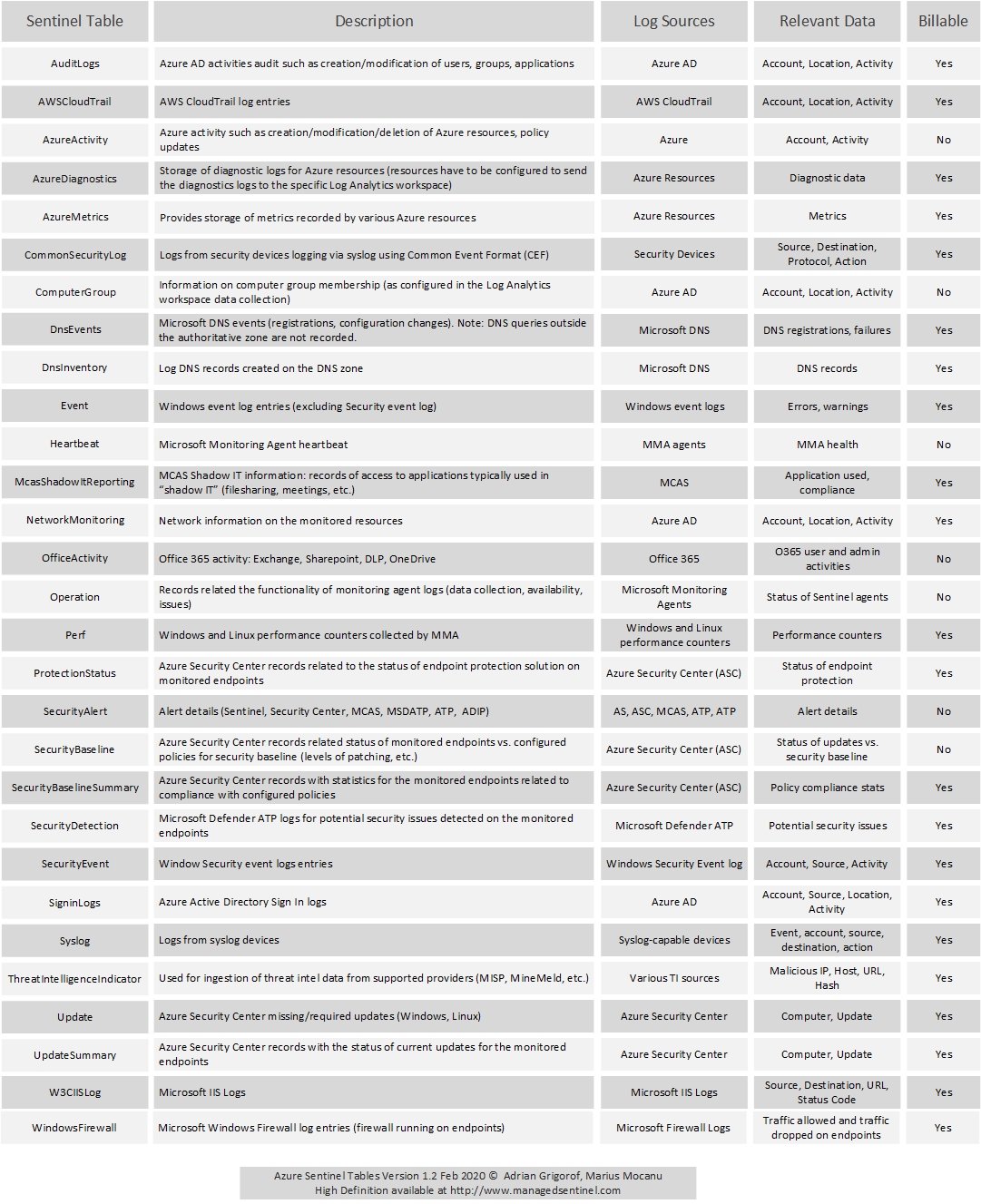
Azure Sentinel is using Azure Log Analytics as the backend for the log storage and querying capabilities through Kusto Query Language (KQL). A wealth of information is available from various log sources and they are stored in Log Analytics “tables”. There are many tables created by default, though not always populated with data and many others that get created when specific Azure Sentinel data connectors are enabled and configured. Another range of tables, not covered in the list below, is represented by custom logs, that can be used to ingest logs from custom applications that don’t fall into the standard SIEM log sources.
The Azure Sentinel Tables diagram provides a list with the most common tables, a description of what they contain, the log sources that populate these tables and the typical data that can extracted from it for analysis purposes. Azure Sentinel is priced by GB/month ingested but not all the data is billable. A significant exception from “billing” is the OfficeActivity table that stores the logging data from Office 365, so one can use Azure Sentinel to monitor Office 365 data without any additional charge.
Contact us for full walk-through of this diagram and a review on how Azure Sentinel addresses most of the challenges faced by the SIEM industry.